Recent Study on Outdated Driver Vulnerabilities, Security Risks & Possible Solutions
An outdated device driver is a common cause of various computer errors, such as the MIDI output issue, error code 0x800F092, and the DRIVER_IRQL_NOT_LESS_OR_EQUAL BSOD error. Aside from these errors, corrupt drivers can also lead to system instability and poor performance.
Hackers use outdated drivers’ flaws to inject malware that can change your CPU and voltage settings, take control of anу device like a USB drive, camera and microphone or just install viruses that cannot be deleted even after Windows reinstall.
Due to outdated drivers, such computer vulnerabilities are becoming more widespread because a lot of users are ignoring the risks, are not aware of these issues, or simply believe it’s not that important.
We have done our own research and now see a drastic increase in the numbers of flaws from 2012 to 2019 by 9000%, from 2 flaws to 150-200 cases every year. That makes outdated drivers’ flaws a growing concern.
- How Hackers Exploit OS Access Levels.
- Statistics of Outdated Drivers’ Flaws
- Case Studies
- How Hackers Exploit Flaws of Outdated Drivers
- How Do You Get Spyware on Your PC?
How hackers exploit drivers flaws
Operating systems like Windows OS have several layers of access level (rings), each having a different set of limitations. These levels are:
- Ring 3 – Applications
- Ring 2 – Device Drivers
- Ring 1 – Device Drivers
- Ring 0 – Kernel
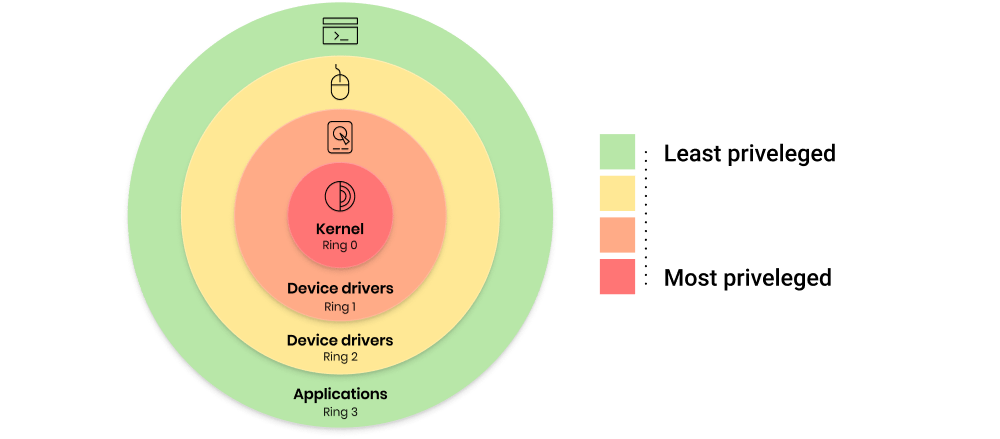
The user mode, also known as the Applications level or ring 3, cannot directly access hardware or reference memory. Any code that is running at this level must ask for permission first to make any changes to the system. This isolation feature offers protection to the inner levels of the system and makes it easier for the computer to recover from crashes.
So if an application freezes or quits suddenly, you can easily get back to what you’re doing after a simple restart. The user mode does not have the ability to modify the system. So, no matter what you do at this level, the system functions won’t be largely affected, and the operating system will not be impacted or broken.
The driver code, found on ring 1 and 2, facilitates communication between the operating system kernel and the hardware. This means that this inner level has more rights and capabilities than the system administrator or user. The driver code is also automatically trusted by the kernel, so any changes done at this level do not require permission.
The next level, ring 0, ‘which’ is the Kernel mode, and is known as the executing code. It has total and unrestricted access to all underlying hardware and rings. It can freely execute any CPU instructions, as well as reference any memory address. Kernel mode is reserved for the innermost level and most trusted functions of the OS. When a crash happens in Kernel mode, it might potentially damage the system.
It can break your OS, and there is a huge chance that you might not be able to recover from it. This ring has direct access to the CPU and the system memory, so any instructions requiring the use of either will be executed here.
Most applications can only access the ring 3 level, and the device drivers belong to ring 1 and 2 with higher privileges. If you have outdated drivers, hackers can exploit them to invade your system and take control of ring 1 and 2. They can go even deeper to the Kernel level (ring 0) to control all the processes on your computer.
The driver code, found on ring 1 and 2, facilitates communication between the operating system kernel and the hardware. This means that the inner level has more rights and capabilities than the system administrator or user. The driver code is also automatically trusted by Kernel, so any changes done at this level do not require permission.
Example of Cyber Attacks Caused by Outdated Drivers
Here’s a scenario: malware controlling a user program in ring 3 cannot easily access hardware devices on your computer. Whether it’s your camera or printer, any software needs your permission to access these devices.
This is because the driver’s hardware access is limited to ring 1 and 2 levels. Thanks to this, malware is prevented from causing major damage to your computer.
Initially, malware only has user rights because it is able to infect applications running in the user mode. Most security products are able to detect and delete it.
If the malware is able to inject itself into the device driver level, the malware controls all driver functions and can even dig deeper to the kernel and Extensible Firmware Interface (UEFI) to drop its code. It also does not need to ask for permission for all of its operations.
UEFI serves as the bridge between the OS and the platform firmware, allowing them to interact and work smoothly with each other. You can think of it as the upgraded version of the BIOS (Basic Input/Output System), the firmware interface that was originally used by IBM computers. Infections at the UEFI level are hard to deal with unless you flash the firmware.
Even if you have the most robust security software, you won’t be able to do anything to get rid of the malware since applications only have ring 3 rights. And most importantly, the malware is able to plant itself in the kernel level and gain full control of your computer.
A perfect example is the Slingshot APT malware. This group took advantage of outdated drivers to gain elevated rights on infected PCs. The Lojax rootkit, also known as Sednit or Fancy Bear, takes root in the UEFI firmware via a signed driver making it more dangerous compared to other malware.
When it comes to malware infection, no computer is safe, no matter how modern your device is. All devices running various Windows versions are vulnerable since nothing can stop device drivers from loading.
Security experts have found that malware can infiltrate even the most up-to-date Windows OS versions’ and they are able to operate without crashing the OS, unlike most kernel-level malware. This is more dangerous because the user is not aware that there is something wrong with the system, and malware has already infected the computer.
In 2019, the security firm, Eclypsium, discovered various flaws in over 40 device drivers from at least 20 different vendors, including ASUS, ASRock, Toshiba, GIGABYTE, Micro-Star International (MSI), Intel, NVIDIA, Realtek, and Huawei, that could be exploited to install a persistent backdoor on Windows computers.
So, outdated drivers can cause the following consequences:
The attacker may be able to control the performance of the peripherals connected to your PC, such as your monitor, keyboard, webcam, speakers, mouse, and USB devices.
- Attackers can damage your hardware by modifying the manufacturer settings, manipulating CPU voltage, and causing your GPU to overheat.
- Hackers may infect the UEFI with a rootkit that survives on the firmware-hardware level. Deleting your operating system or wiping the hard drive will not help unless the firmware is reflashed to delete the malicious component. If reflashing the UEFI is not possible, your only option is to change the motherboard of the infected computer.
- If the infected PC is a part of a network or IoT system, the attackers can take over all of the network devices and mechanisms. For example, the complex computer worm, Stuxnet, infected the computers at Iran’s first nuclear power station in 2010. The Stuxnet worm is known for its ability to seize control of industrial plants, including systems used to manage oil rigs, water supplies, power plants, and other utilities.
- Your computer can be injected with a cryptominer or malware that would use your computer resources for DDoS attacks.
- Hackers can use this to get access to your personal data. Even if you protect your data with strong encryption, the attacker can simply drop undetectable spyware on your system that can record every stroke on your keyboard or every piece of data you enter. Alternatively, they can infect your computer with ransomware and simply overwrite the encryption, which means that you will also lose access to your files or the system itself.
For these reasons, keeping all your drivers updated is essential for your PC’s security and performance. Instead of wasting your time performing manual driver checks, you can use Driver Updater to keep all your drivers up-to-date automatically.
Statistics of Outdated Drivers’ Flaws
Let’s take a look to some common vulnerabilities observed by cybersecurity experts today:
- Escalation of Privileges – involves exploiting a flaw to get access to protected system functions, giving the attackers complete control over a machine.
- Information Disclosure – means collecting and leaking information about the user and the system.
- Denial of Service – this attack makes the computer unusable and is often characterized by hardware/software errors, freezing, crashing, and blue screens.
- Code Execution – the attacker sends commands or executes code on the computer using a trusted process.
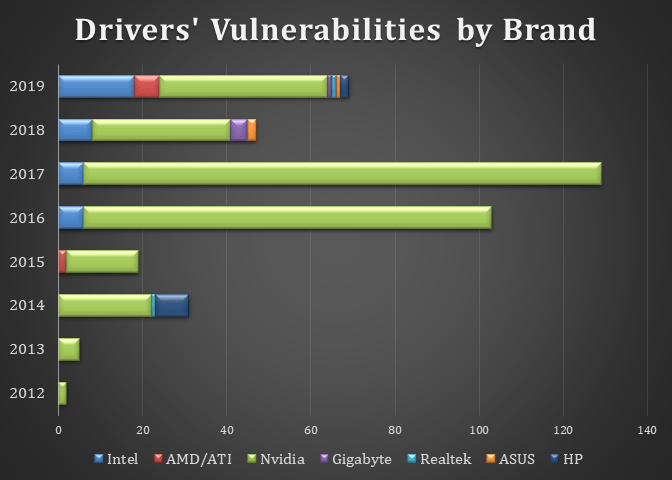
The image below reveals a huge increase in the number of drivers’ flaws between 2006 and 2019, from only 4 cases in 2006 to an average of 87 cases every year. 2016 stands out because of the abrupt rise in cases from 19 to 103, which makes it more than a 5x increase in a single year.
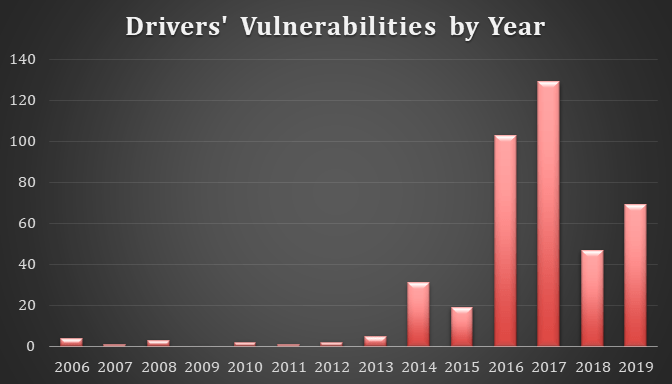
NVIDIA has the highest number of flaws year-on-year, compared to other brands. Huge spikes in the number of flaws can also be noted, starting 2016. Surprisingly, Realtek has the least number of flaws, with the first three cases occurring only in 2019.
In terms of flaw diversity, the only known flaw in 2012 was the Escalation of Privileges. But year after year, attackers keep on getting more creative, and other types of vulnerabilities are being discovered. In 2019, aside from escalation of privileges, other flaws exploited by hackers include Information disclosure, Denial of Service, and Code Execution.
As the types of flaws get more diversified over the years, their total market share also changes. For example, escalation of privileges had total dominance in 2012, but it gradually dropped to 32% in 2019. Denial of service is one of the fastest rising types of flaws, jumping from 0% in 2012 to 50% in 2014. Code Execution’s share has also quadrupled, from 6% in 2017 to 24% in 2018 and 21% in 2019.
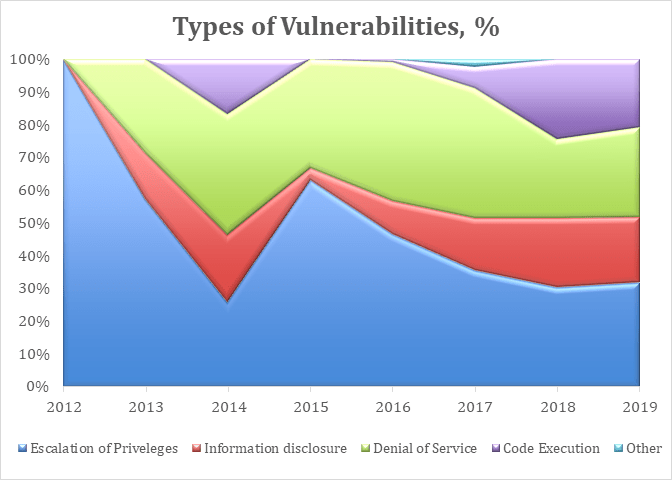
Overall, the increasing number and diversity of flaws highlight the importance of keeping your device drivers updated at all times.
You can find all the data sources we used to prepare this research here.
Case Studies
Ransomware Attack Due to Outdated Gigabyte Motherboard Driver

This attack was discovered by security company Sophos and involved two separate ransomware attacks where a genuine, digitally signed driver was employed.
The attackers deployed a software package published by Gigabyte that has a known vulnerability, called CVE-2018-19320. The ransomware first deletes the security products from the infected computers before proceeding with the file encryption.
The cybercriminals used the Gigabyte driver to load a second unsigned driver that kills all processes and deletes files associated with security products to enable the ransomware to work without interference.
In order to prevent attacks like these, Sophos Labs recommended:
- Using multi-factor authentication (MFA), complex passwords, and a password manager
- Limiting access rights so that user accounts and admins only have the access rights they need
- Making regular backups and storing them off-site and offline
- Locking down your Remote Desktop Protocol (RDP) ports
- Enabling tamper protection
Widespread Insecure Drivers in 2019
Eclypsium Security discovered in 2019 that more than 40 drivers from at least 20 vendors are outdated and insecure. The list includes major BIOS and hardware vendors. What makes it worse is that all the vulnerable drivers were certified by Microsoft.
Here is a complete list of the affected vendors:
- ASRock
- ASUSTeK Computer
- ATI Technologies (AMD)
- Biostar
- EVGA
- Getac
- GIGABYTE
- Huawei
- Insyde
- Intel
- Micro-Star International (MSI)
- NVIDIA
- Phoenix Technologies
- Realtek Semiconductor
- SuperMicro
- Toshiba
Vulnerable or outdated systems are a widespread concern, making these outdated devices a high-value target for cybercriminals who can use this vulnerability to launch other attacks, brick the OS, or collect data from the user.
Intel Graphics Drivers

This issue particularly involves desktops and laptops with integrated graphics. Intel has patched multiple high-severity vulnerabilities in its graphics drivers, along with other flaws in its NUC firmware that could allow hackers to steal sensitive data.
These flaws, if exploited, permit a privilege of escalation, denial of service (DoS), and information disclosure. The worst flaw is the buffer-overflow vulnerability or CVE-2020-0504, which could potentially allow an authenticated user to enable a denial of service through local access. Aside from six major high-severity flaws, Intel has also addressed 17 more vulnerabilities through that patch.
HP Touchpoint Analytics Drivers

HP TouchPoint Analytics is a pre-installed service that gathers diagnostic information about the device’s performance. The vulnerability actually lies in the Open Hardware Monitor, the software that monitors fan speeds, voltages, temperature sensors, load, and clock speeds of the computer. It is a third-party component of HP Touchpoint Analytics and is used on tens of millions of computers.
Open Hardware Monitor does not properly inspect DLLs before running them, which gives DLL hijackers an opportunity to execute malicious payloads on the machines using a signed service, basically whitelisting those malware.
Nvidia GeForce Drivers

Multiple high-severity vulnerabilities in Nvidia’s GPU display drivers could be exploited by attackers for code execution, DoS attacks, and file corruption.
Nvidia previously patched six flaws that impact both Windows and Linux operating systems. Nvidia’s GeForce graphics cards and GeForce Experience software are used to optimize game settings, manage drivers, and for live streaming.
AMD ATI Radeon Drivers

Updating your AMD Radeon drivers should be done as soon as updates are released to prevent security issues. The company recently released a patch secretly to fix four major security flaws impacting Radeon GPUs, particularly the Adrenalin 20.1.1 drivers.
The vulnerabilities are listed as CVE-2019-5124, CVE-2019-5146, CVE-2019-5147, and CVE-2019-5183.
This vulnerability in the AMD Radeon driver involves the ATIDXX64.dll file, which could be exploited to perform denial of service attacks or remote code execution. What’s worse is that this attack vector can be deployed to exploit the host machine from a VM.
Realtek Audio Drivers

Realtek drivers are installed in most computers, including desktops and laptops.
A critical flaw in the HD Audio Driver Package driver for Windows was discovered by the vulnerability testing team at Realtek, tracked as CVE-2019-19705. It can be exploited using DLL hijacking to execute malicious scripts.
The vulnerability involves the HD Audio Background Process or RAVBg64.exe, which runs as NT AUTHORITY\SYSTEM. After loading, the process tries to load the missing DLLs: RAVBg64ENU.dll and RAVBg64LOC.dll its own directory.
How Hackers Exploit Flaws of Outdated Drivers
Fortunately, there is still no way to identify outdated drivers by remote scanning via IP address. Hackers won’t be able to find out your drivers are outdated unless you are being targeted specifically.
Right now, network scanning apps, such as Nmap and OpenVAS, let you search by IP address and provide reports on your device type, open ports, IP provider, reverse DNS names, and MAC address. Wireshark, another popular network scanner, is capable of snooping on data transmitted via public Wi-Fi networks, as well as recording and analyzing data packets.
Search engines, including ZoomEye and Shodan, are able to discover network connections around the world and gather information. They can see where an IP address is geographically located. However, they won’t have access to your system information or the status of your drivers.
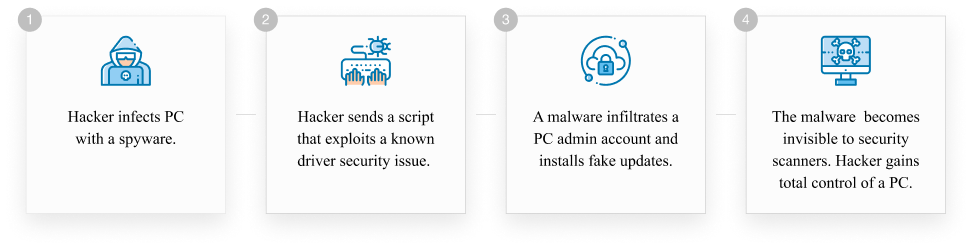
In order for attackers to gain full control of your system, any of the following scenarios should occur:
- Spyware has been installed on your computer to scan your system settings and driver versions. The hacker uses the spyware to establish a backdoor to send the malware through and download additional payload.
- The hacker sends a script that exploits a known driver security issue via existing spyware on your PC.
- Malware infiltrates an admin account and installs fake updates on the computer. The fake updates might be detected and deleted by robust security software with an updated database.
- The malicious script is merged with a trusted driver process that has the power to initiate critical system changes. The malware also becomes invisible to security scanners because it operates on an inner system ring. If this happens, the attacker gains total control of the operating system.
An effective way to minimize the impact of malware is by creating two accounts on your computer: the Admin and User/Guest accounts. The Admin account should be used solely for making system changes while the User/Guest account should be used for everyday processes.
This setup might be a hassle, but it does provide another layer of protection against malware that is able to elevate Admin rights by using buffer overflow vulnerability.
Malware that has been installed using the User/Guest account will need to request admin permission to update or perform other tasks. If you grant a request using an Admin account, then it’s the same as giving the malware free rein over your operating system.
Applications generally use the access permissions of the account used for executing the program. By default, Windows uses Admin accounts on PCs, but you can easily create a new User or Guest account for everything else.
However, most malware variants do not need administrator rights in order to run. According to research conducted by CyberArk, though many malware variants require Administrator rights to execute properly, 90% don’t need them.
That is why it is hard to determine when malware infects your computer unless you detect the symptoms. Unfortunately, it might take several days to several weeks before you actually notice the presence of malware that was obtained by utilizing a known driver flaw.
How Do You Get Spyware on Your PC?
All outdated drivers’ flaws come from ordinary spyware injection into a target PC. There are several ways for spyware to infiltrate your system. It can be as simple as opening a secure website that hosts the spyware or as trivial as opening spammy links and attachments. But most of the time, spyware is bundled with freeware or shareware you download from the internet and install on your computer.
Here are some of the known distribution techniques hackers employ to spread spyware:
- Remote Desktop Protocol (RDP) and Port Scanning
- Phishing
- Fake Software Updates
- Torrenting
- Insecure Wi-Fi Networks
- Cross-Site Scripting (XSS) Attacks
- Unpatched Software
- Hidden USB Devices
- Social Media
- Bluetooth/Internet of Things devices
- Mobile Devices with OS Vulnerabilities
Conclusion
Some users consider updating their device drivers a tedious process that they just need to get over with. In fact, the case studies discussed above show how few users and companies, including major corporations, actually install software updates. Updating your device drivers not only keeps your device working smoothly but also protects you from attacks that target software vulnerabilities. As the saying goes, prevention is always better than cure.
Use only trustworthy sources to update your PC drivers. You can keep all your drivers up-to-date automatically with one universal tool: Driver Updater. It scans your computer for outdated drivers, then retrieves the latest versions from official manufacturers that would perfectly work with your PC.