VPN privacy is often misunderstood – people expect total anonymity, but the reality is far more complex.
Imagine you’re a 17-year-old trying to get into a bar with a fake ID (which we strongly condemn). You told your parents you’re staying at a friend’s, slipped past the bouncers, even ordered a frothy pint—mischief managed—until you remember the CCTV cameras outside and that your dad’s best friend is a cop…

Hope you catch my drift—it’s pretty close to how VPNs work: they protect your privacy by letting you mask your location from ISPs and website owners (the parents), bypass geo-blocking (the bouncers), and snag that subscription for a few bucks less (the drink). But they won’t change your identity, which can still be traced back to you via logs, browser fingerprinting, or data leaks. So, is true anonymity a myth?
As VPN adoption rapidly grows—with the U.S. leading the pack at over a 40% VPN usage rate—so do concerns about VPN privacy risks. In our previous article, we explored how VPNs work and broke down their key security features. Now, let’s talk privacy—see how VPNs hide your online footprint, trace the history of data leaks and legal battles (we’ve got the names!), and find out whether it’s even possible to stay incognito online today.
Can VPNs Really Make You Anonymous?
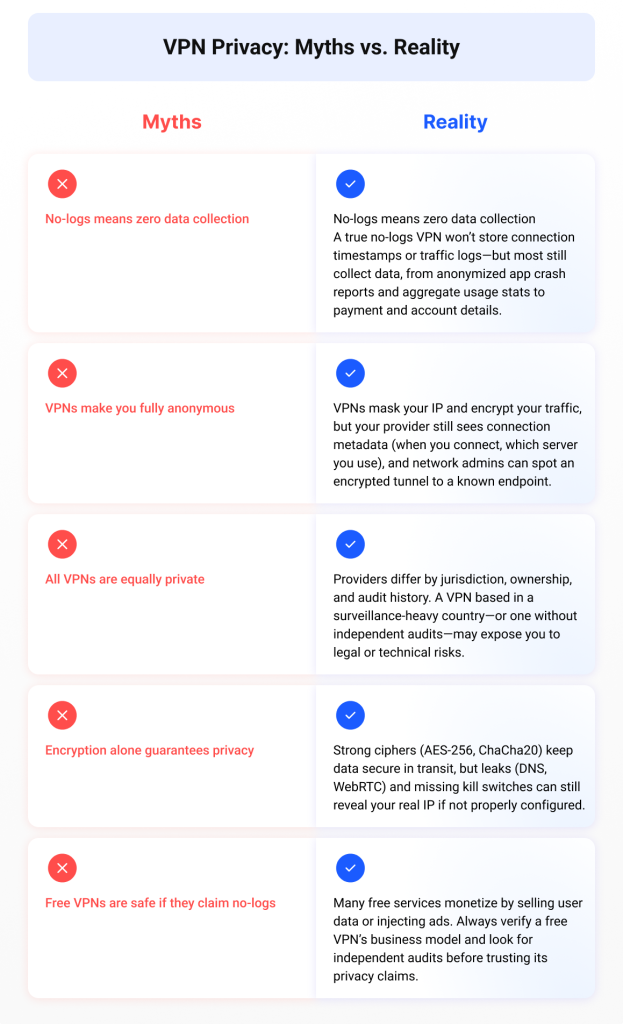
I bet not many of us could list the differences between privacy and anonymity off the top of our heads. But the distinction is significant: privacy means keeping your activities to yourself, while anonymity is about hiding who you are. VPNs excel at the first—encrypting your internet traffic and masking your IP address—but they don’t make you completely anonymous. Let’s clear up some common misconceptions right off:
What people get wrong about VPN privacy
For a reality check, try visiting deviceinfo.me to see what your device shares: model, OS, location, network details. Enable your VPN, and only your IP, location, and network info change—everything else stays the same. So much for anonymity…
VPNs Can’t Hide Everything
Browsers don’t help either. Log into Chrome with your Google account, and Google tracks all your browsing—even the best VPN for privacy and security won’t stop that. Add cookies and browser fingerprinting, and sites can still piece together who you are.
📃Note:
🕵️Do you really know how much they know?
When you visit a website, it automatically (thanks a lot, JavaScript) shares a bunch of details—like your screen resolution, time zone, system fonts, installed plugins, hardware specs, and even your device’s battery status and which extensions you use.These are stitched into a unique fingerprint that’s very hard to fake or mask. Then this data—depending on who’s interested—can be used to offer you products that feel hand-picked just for you or, if you’re less lucky, to help build a profile on you as part of broader tracking or even identity theft.
However, this doesn’t mean you’re out in the open when using a VPN. Multiple factors affect your privacy level—jurisdiction, logging policies, data leak protection, VPN protocols, and even your provider’s parent company—but steering clear of strict VPN jurisdictions and VPN providers that keep logs or have a history of leaking user data should keep you under the radar in most cases.
💡Want to know what exactly your browser shares?
Check out this tool, which shows how well you are protected from tracking and fingerprinting.
Key VPN Privacy Risks You Should Know
Next up, let’s look at the most common VPN privacy risks that could expose your data or identity:
1. Jurisdiction
Don’t overlook where your VPN provider is headquartered. If it’s based in a country with tight data retention laws or part of the Five/Nine/Fourteen Eyes alliances, think twice. The same goes for any parent and sister companies, as they may share user data. Want to know who owns your VPN and which country it is accountable to? Check its privacy policy or look it up on Crunchbase.
2. Logging policies
Most providers claim to be a VPN with a no-logs policy, but take it with a grain of salt. Read the fine print—some may still stash timestamps, bandwidth usage, or even browsing history. This is especially true for free VPNs, most of which make a living by selling your data.
3. Weak encryption
We covered this in depth in our article on VPN security, so here’s the quick scoop: always pick VPNs using AES-256 or ChaCha20, and steer clear of PPTP, L2TP/IPSec (in older configurations), or any cipher known to crack under pressure.
4. IP, DNS, and WebRTC leaks
Without IPv6, DNS, and WebRTC leak protection, your ISP has the front-row seat to your browsing, and your IP address is on full display.
5. No kill switch
If your VPN lacks a reliable kill switch—or if the feature is buggy—any drop in the tunnel can instantly expose your true IP to websites and your ISP. Your ISP may also see which sites you’re visiting—at least at the domain level—especially if DNS leak protection doesn’t kick in either. So always test it across your devices before trusting it with sensitive work.
6. Server storage:
RAM-only servers wipe every bit of data on reboot, making them a privacy champion. Most top VPNs now use them—except Proton VPN, which intentionally sticks with full-disk encryption, arguing it offers equivalent protection.
Like mentioned before, no-logs policies and jurisdictions are two major factors of VPN privacy. So let’s get into detail.
VPN Privacy Policies: What Do They Really Say?
It’s rare to find a provider that doesn’t claim to be the best no-log VPN. But should we take their word for it? Sure, good relationships are based on trust, but that’s not exactly the case here. Some might call it manipulation; others, marketing. One story that comes to mind is UFO VPN—a zero-log provider that leaked millions of logs, including user passwords. So what do VPN providers actually mean when they talk about having a no-logs policy? Let’s dive in and see.
What Counts as VPN Logs?
What are “logs,” to start with? Generally, the term refers to records about your VPN usage that could be used to identify or reconstruct your activity. The main types are:
- Connection logs: timestamps (when you connect/disconnect), the VPN server you used, your original IP address, and session duration.
- Usage (or traffic) logs: the actual data you send and receive—e.g., the websites you visit, files you download, or DNS queries you make.
DNS logs: a record of every domain name you looked up while connected.
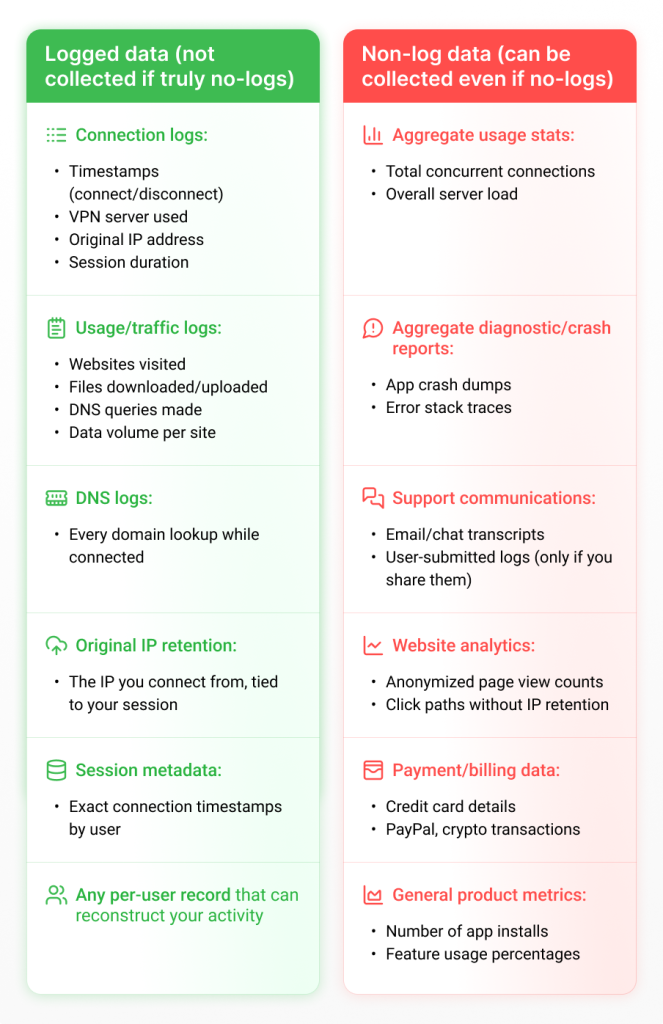
Technically, anything in the left column can be used to reconstruct your individual VPN activity—or even your identity. A no-logs policy means the VPN provider pledges not to store any of those records. In practice, a truly no-log VPN will have none of them on its servers—so even if compelled by a court, there’s nothing they can hand over.
This might sound sweet so far, but there’s a fly in the ointment: “no logs” doesn’t equal “no personal data collected.” Most VPNs still store your account details, like email address and payment info (yes, that means your credit card number can be subpoenaed), along with anonymous usage statistics. On the surface, these bits of data aren’t logs, but if they fall into the wrong hands, they can be matched back to your VPN account and, ultimately, to your identity.
When “No Logs” Isn’t Enough
Imagine law enforcement or a malicious actor subpoenas the provider or exploits a breach and gains access to users’ emails, usernames, payment details, and other data. By cross-referencing that with website logs, cookies, personal account logins, online behavior, payment history, and other “fingerprints,” they can piece together a solid profile that links back to your real-world identity—turning a “no-logs” claim into little more than a paper shield against someone holding a lit match.
Who’s Actually Protecting Your Privacy?
Alright, stoking fear wasn’t by design. To set the record straight, we reviewed the privacy policies of the 12 select VPNs (we started comparing them in the previous article) and drew up a table showing what data each provider collects and stores and whether their policies are backed by independent audits.
| VPN | Collected/stored data | Yes, multiple | Additional notes |
|---|---|---|---|
| Proton VPN | Account info: email address (optional) Payment data: credit card (name, last four digits), PayPal, Stripe, Bitcoin Device info: OS, device model (aggregated, anonymized) Support communications: chats, emails, bug reports (stored for troubleshooting and quality analytics; used internally) App usage: crash reports (if opted in, anonymized), aggregate usage statistics (anonymized) | Yes, multiple | Supports anonymous payments (crypto, cash) No browsing history, DNS queries, or traffic logs stored |
| NordVPN | Account info: email address, subscription details Payment data: credit card (date of purchase, credit card owner’s full name, part of the credit card number, expiration date), third-party services (date of purchase, payer’s IP address, postal code, credit card owner’s full name, and credit card information) Device info: OS, app version, time zone, country (if opted in, anonymized) Support communications: emails, tickets (stored for support purposes) App usage: crash reports (if opted in, anonymized), aggregate usage statistics (anonymized) | Yes, multiple | Supports anonymous payments (crypto, gift cards) No traffic logs, IP addresses, or browsing data stored |
| ExpressVPN | Account info: name, email address, password (hashed) Payment data: credit card (name, billing country, billing address, credit card number), PayPal, BitPay, Paymentwall, Stripe Device info: type, OS, language, user agent, mobile identifiers (anonymized) Support communications: support emails, chats, tickets (stored internally) App usage: crash reports (if opted in, anonymized), aggregate usage statistics (anonymized) | Yes, more than anyone in the industry | Supports anonymous payments (crypto, gift cards) No activity logs, browsing history, or connection logs stored |
| Surfshark | Account info: email address, password (hashed), account registration date, IP address (when Smart DNS is used), aggregated number of performed searches (when Search is used) Payment data: credit card (part of the credit card number, payer’s IP, amount, currency, expiration date), third-party services (transaction date, payer’s IP address, credit card number, credit card owner’s full name) Device info: device identifiers, app diagnostics (anonymized) Support communications: emails, chats (stored for service improvement) App usage: crash reports, performance metrics (aggregated, anonymized) | Yes, multiple | Supports anonymous payments (crypto) No browsing history, session information, or IP addresses stored |
| CyberGhost | Account info: name, address, email address, chosen username Payment data: credit card (name, address, card number, expiration date, email address collected by third-party payment processors), Cleverbridge, Stripe, PayPal Device info: device type, OS, language (aggregated, anonymized) Support communications: support tickets, feedback (stored internally) App usage: aggregate usage statistics (anonymized) | Yes, multiple | Supports anonymous payments (crypto) No traffic logs, browsing history, or IP addresses stored |
| VyprVPN | Account info: name, email address, username, password, IP address, phone number, contact preferences, contact or authentication data, billing address Payment data: credit card (payment instrument number and the security code associated with the payment instrument), PayPal, Chase Paymentech, Intuit Device info: device type, OS, language (aggregated, anonymized) Support communications: in-person, online, phone, mail support interactions; customer surveys and contests | Yes, in 2018 | No anonymous payment options No data retention for connections or DNS |
| Private Internet Access (PIA) | Account info: email address, state/territory, zip code Payment data: credit card (via processor), PayPal, cryptocurrencies Device info: device identifiers, system information (if opted in) Support communications: chats, tickets, emails (stored internally) App usage: aggregate usage statistics (anonymized) | Yes, in 2022 | Supports anonymous payments (crypto, gift cards) No traffic logs, IP addresses, or browsing data stored |
| Windscribe | Account info: email address, state/territory, zip code Payment data: credit card (via processor), PayPal, cryptocurrencies Device info: device identifiers, system information (if opted in) Support communications: chats, tickets, emails (stored internally) App usage: aggregate usage statistics (anonymized) | No published third-party audit to date | Supports anonymous payments (crypto) No IP or browsing logs stored |
| TunnelBear | Account info: email address, account status, X ID (optional) Payment data: credit card (last name, last four digits, purchase date, billing address, expiration date), PayPal Device info: OS version, device type (aggregated) App usage: aggregate usage statistics (anonymized) | Yes, multiple | No anonymous payment options No traffic, DNS query, or browsing activity logs stored |
| Hotspot Shield | Account info: name, username, email address, password Payment data: credit card (billing name, billing address, credit card details), PayPal Device info: device identifiers, OS, hardware model Support communications: support requests, feedback (stored internally) App usage: session duration, bandwidth | Yes, in 2023 | No anonymous payment options No browsing history or online activity logs stored Collects device and session data for performance monitoring |
| Norton VPN | Account info: name, mailing address, email address, phone number, username and password Payment data: credit card (billing name, billing address, credit card details), PayPal (payment data) Device info: OS version, device ID, IP address (temporarily for session) Support communications: customer support via chats, emails, calls App usage: usage data, diagnostic data | No published third-party audit to date | No anonymous payment options Limited session logging (IP address temporarily for connection) No browsing content logs stored |
| Mullvad | Account info: randomly generated account number (no email required) Payment data: bank wire (sender name, address, bank account number, Mullvad account number), PayPal (transaction ID, sender name, origin country, email address), Swish (Swish ID, name, phone number), Stripe (Stripe charge ID, expiration date, last 4 digits of the card, card type, origin country) Device info: none (no personal device identifiers collected) Support communications: support emails (if sent) App usage: no app usage logs, optional crash reports (redacted program logs, app version, and operating system) | Yes, multiple | Supports anonymous sign-up (doesn’t require email) Supports anonymous payments (crypto, cash) No connection logs, traffic logs, or identifying data stored |
This table shows that saying something isn’t the same as doing it. One thing is clear: a VPN with a no-logs policy is a crown you have to earn (and validate!). Mullvad clearly stands out for its commitment to user privacy—anonymous signup and payment, repeated audits, and no identifying data collection.
But it doesn’t end with policies. Every VPN claims to be on the front lines of privacy—until it faces government orders. Depending on the jurisdiction, your VPN may be forced to hand over data to authorities—or worse, intelligence agencies might not even need a court order; they could simply seize it. Let’s get into it.
VPN Jurisdictions: Why Location Matters
VPN jurisdiction is another important metric that shows you how much a provider cares about privacy. Even with no-logs promises and independent audits, many users remain wary of certain places.
This includes Five/Nine/Fourteen Eyes members—and countries such as Russia, India, and China, which impose strict surveillance laws on VPN providers.
What are Eyes alliances?
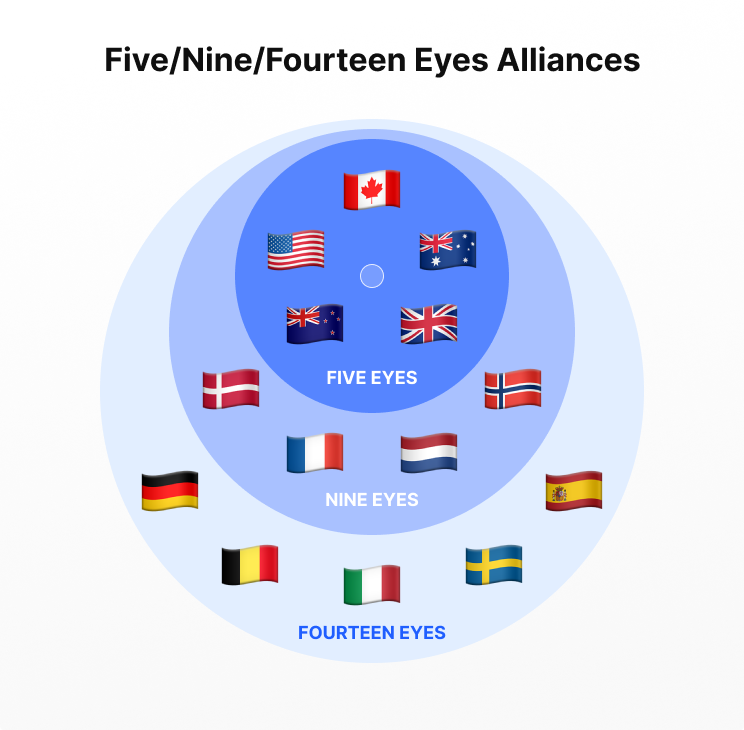
A lot has been said about the Eyes alliances in relation to VPN services. Most reviews advise steering clear of these jurisdictions as a precaution. That’s because the U.S., the main architect of these treaties, has been embroiled in surveillance and invasive privacy scandals in the past. So there’s always a risk that countries that have agreed to share intelligence with the U.S. can also cooperate to force VPNs to give up user data.
Laws like the Patriot Act also reinforce people’s wariness about using U.S.-based VPNs.
However, it’s not all doom and gloom. Yes, they can seize servers without a court order and share data across the globe. However, the idea behind the alliance is not to snatch torrent downloaders, but to allow participating countries to share intelligence as part of their counter-terrorism efforts. And so far, no Eyes member has enacted laws explicitly forcing VPN providers to retain or share user logs.
Moreover, even in countries like Panama, championed as one of the best jurisdictions for VPNs, authorities can serve legal orders asking VPN companies to give up the data they collect. Another strong VPN jurisdiction for privacy, Switzerland, has been weighing amendments to its surveillance laws that could require VPN providers to collect and store user data and cooperate with government requests.
Given all of the above, providers that do not log user data will simply have no data to hand over. And companies like Windscribe—headquartered in Canada, a Five Eyes country—proudly publish their refusal or inability to comply with government requests for data. One, because they are not legally obligated to do so. Two, because they don’t have the data to submit.
Best countries for VPN privacy
What can we say based on the info we’ve gathered? Although countries like Switzerland, Panama, the British Virgin Islands, Lithuania, Iceland, and Estonia, among others, are promoted as the best countries for VPN headquarters, they’re mostly viewed favorably due to historically low incidents of government overreach rather than specific laws.
Other established market economies, even those in Eyes alliances, generally don’t clamp down on VPN companies. Anyway, before making a decision on a VPN provider you’ll trust your privacy to and share your data with, research its headquarters and the data retention laws that govern them. But when speaking of jurisdictions, there’s still another elephant in the room…
What about parent companies?
Most major VPNs today aren’t self-reliant services. In fact, among the reviewed VPNs, only Windscribe and Mullvad appear to be still owned by their founders. Others are assets of larger companies. And this dependence poses another privacy risk if a provider shares user info with its parent or sister companies. For example, Proton VPN, NordVPN, ExpressVPN, CyberGhost, Hotspot Shield, and Norton VPN clearly indicate that through their privacy policies, but I’d just accept it as fact for any provider.
The thing is, these parent and sister companies may be located in countries different from the VPN itself. So to make an informed decision, you still need to know the jurisdictions of these companies. Reading through their privacy policies will also help you understand how they handle and share your data.
Jurisdictions & privacy risks
| VPN | Jurisdiction | Parent company (Jurisdiction) | Comment on jurisdiction | Eyes alliance |
|---|---|---|---|---|
| Proton VPN | Switzerland | Proton AG (Switzerland) | Strong privacy laws and outside surveillance alliances | No |
| NordVPN | Panama | Nord Security B.V. (The Netherlands) | Panama has no data retention laws and is not part of any surveillance alliance The Netherlands has strong GDPR protections and no mandatory data retention laws, but is part of Nine Eyes and allows intelligence agencies to conduct bulk surveillance under the Wiv 2017 | No (Panama) Nine Eyes (The Netherlands) |
| ExpressVPN | British Virgin Islands | Kape Technologies (UK) | BVI favors privacy rights, has no data retention laws, and is not a member of any surveillance alliance The UK is part of Five Eyes and has broad surveillance laws (Investigatory Powers Act) | No (BVI) Five Eyes (UK) |
| Surfshark | The Netherlands | Nord Security B.V. (The Netherlands) | The Netherlands has no data retention laws but is part of the Nine Eyes alliance Nine Eyes (The Netherlands) | Nine Eyes (The Netherlands) |
| CyberGhost | Romania | Kape Technologies (UK) | Romania has strong GDPR protections, no mandatory data retention laws, and isn’t part of any surveillance alliances The UK is part of Five Eyes | No (Romania) Five Eyes (UK) |
| VyprVPN | United States | Certida LLC (United States) | The U.S. is part of the Five Eyes alliance and its laws (like the Patriot Act) are intrusive, but they don’t require VPNs to retain data | Five Eyes |
| Private Internet Access | United States | Kape Technologies (UK) | Both the U.S. and the UK are part of the Five Eyes alliance | Five Eyes |
| Windscribe | Canada | Windscribe Limited (Canada) | Canada is a Five Eyes member but does not have data retention regulations intended for VPN companies | Five Eyes |
| TunnelBear | Canada | McAfee (United States) | Both Canada and the U.S. are part of Five Eyes but do not impose data storage laws on VPNs | Five Eyes |
| Hotspot Shield | United States | Pango Group (United States) | The U.S. is a Five Eyes member and has intrusive surveillance laws, despite no legal VPN retention laws | Five Eyes |
| Norton VPN | United States | NortonLifeLock (United States) | The U.S. is a Five Eyes member and has intrusive surveillance laws, despite no legal VPN retention laws | Five Eyes |
| Mullvad | Sweden | Amagicom AB (Sweden) | Sweden has strong GDPR protections and no mandatory data retention laws but is part of Fourteen Eyes | Five Eyes |
As it appears, Proton VPN is the only service on our list that’s not part of surveillance alliances. But ultimately, regardless of jurisdiction, if a government really wants data, it can seize it—so your best bet is to stick with a VPN that collects the bare minimum and truly keeps no logs.
VPN History of Data Breaches & Legal Challenges
Admit it—you’ve heard of massive data leaks, security breaches, and other sorts of hacks. Major VPNs haven’t been immune, facing scandals from server hacks and government seizures to regulatory complaints. While none of these incidents led to mass user data exposure, they’ve strengthened trust by forcing providers to prove (or upgrade) their privacy measures.
I promised you names—here are the most notable events and how each VPN responded.
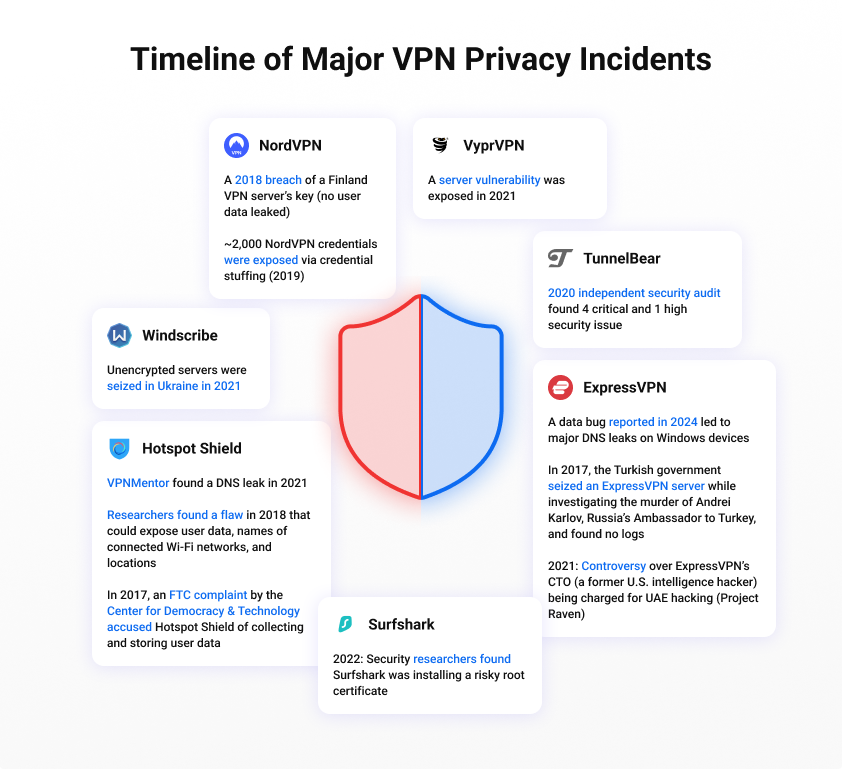
Timeline of Major VPN Privacy Incidents
| VPN | Incident/controversy | Response |
|---|---|---|
| NordVPN | A 2018 breach of a Finland VPN server’s key (no user data leaked) ~2,000 NordVPN credentials were exposed via credential stuffing (2019) | NordVPN shredded the server after receiving an alert from the third party NordVPN claimed to have started working on extra measures to enhance rate limiting |
| ExpressVPN | A data bug reported in 2024 led to major DNS leaks on Windows devices (no user data leaked) In 2017, the Turkish government seized an ExpressVPN server while investigating the murder of Andrei Karlov, Russia’s Ambassador to Turkey, and found no logs 2021: Controversy over ExpressVPN’s CTO (a former U.S. intelligence hacker) being charged for UAE hacking (Project Raven) | Split-tunneling was restored to Windows after the problem was resolved The server did not expose any user data due to ExpressVPN’s no-logs policy ExpressVPN said it had no problem with the former intelligence operative protecting the privacy of its customers |
| Surfshark | 2022: Security researchers found Surfshark was installing a risky root certificate | Surfshark responded to TechRadar, claiming to have fixed the problems |
| VyprVPN | A server vulnerability was exposed in 2021 | VyprVPN said it fully resolved this problem |
| Windscribe | Unencrypted servers were seized in Ukraine in 2021 | Windscribe immediately improved its server-side encryption and published a commentary, admitting that the server was not encrypted and highlighting the fact that user data was not compromised since Windscribe does not log user traffic information |
| TunnelBear | 2020 independent security audit found 4 critical and 1 high security issue | These issues were fixed, according to the report |
| Hotspot Shield | VPNMentor found a DNS leak in 2021 Researchers found a flaw in 2018 that could expose user data like names of connected Wi-Fi networks and locations In 2017, an FTC complaint by the Center for Democracy & Technology accused Hotspot Shield of collecting and storing user data | Since Hotspot Shield’s acquisition by the Pango Group in 2024, it has claimed to revamp its privacy policy to follow the best standards Hotspot Shield reported that it has fixed the Wi-Fi vulnerability |
As you can see, no VPN is entirely immune to external pressures – whether srver vulnerabilities or legal seizures—but transparent responses, swift technical fixes, and verifiable third-party audits remain the industry’s best defenses against compromising user privacy.
Final Verdict: The Best VPNs for Privacy
So, which VPNs truly guard your secrets instead of just talking a good game? When it comes to privacy, we’re looking for rock-solid no-logs pledges, ironclad jurisdictions, and a track record of saying “no data here” even under pressure. Toss in independent audits, RAM-only servers, and obfuscation features that hide VPN use itself, and you’ve got the privacy dream team. Ready to see who keeps your digital footprint truly under wraps?

Best VPNs with no logs in 2025
The best no-log VPNs are those audited by reputable independent firms. Multiple audits are also a plus, as each only captures a snapshot in time and isn’t foolproof for long-term trust.
Here’s how the VPNs rank based on their no-logs audit track records:
- ExpressVPN: 18 independent no-logs audits.
- NordVPN: Five independent no-logs audits. Completed its fourth audit in 2023 and the fifth in late 2024.
- Mullvad: Four independent security audits. Completed the most recent one in 2024.
- Proton VPN: Three consecutive third-party no-logs audits as of July 18, 2024.
- CyberGhost: Two independent no-logs audits as of 2024.
- Private Internet Access: Completed its second independent no-logs audit in 2024.
- Surfshark: Completed its first independent audit in 2023.
- VyprVPN: One independent audit back in 2018.
- Hotspot Shield: Conducted an independent security audit in 2023 that verified its no-logs policy.
- Windscribe: Ran a security audit for its new VPN stack called FreshScribe in 2022 that verified its no-log policy.
- TunnelBear: Completed seven independent security audits, but none specifically verifying a no-logs policy.
- Norton VPN: Ran an independent no-logs audit in 2024, according to CNET, but is yet to publish the document or findings.
While racking up more audits looks impressive, remember that to determine the best VPN that keeps no logs, it’s equally important to see how transparent the provider is about the audit results—and how quickly it fixes any flaws that get exposed.
Best VPN headquarters locations
The best VPN headquarters locations are in privacy-friendly countries outside surveillance alliances, with no mandatory data retention laws, and with little to no history of incidents like server seizures.
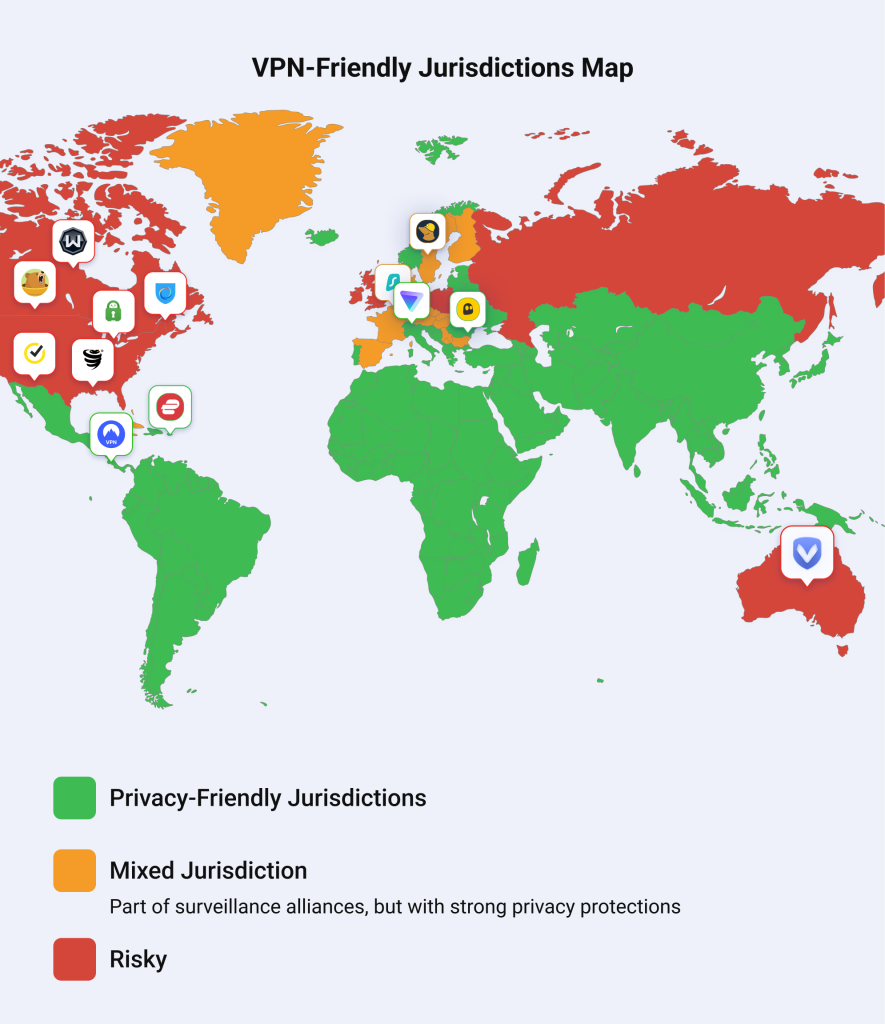
Among the VPNs we’re covering here, Switzerland (Proton VPN), Panama (Nord VPN), the British Virgin Islands (ExpressVPN), and Romania (CyberGhost) top the list as the safest havens for VPNs thanks to their respect for user privacy.
Sweden (Mullvad) and the Netherlands (Surfshark) are part of the Fourteen and Nine Eyes alliances, respectively, but still hold strong thanks to GDPR protections and the absence of mandatory data retention laws.
Meanwhile, the U.S. (VyprVPN, PIA, Hotspot Shield, and Norton VPN) and Canada (Windscribe and TunnelBear) don’t force VPNs to store data, but both countries are part of the Five Eyes alliance—and have a reputation for being rather nosy when it comes to user privacy.
Finally, don’t forget to check the headquarters location of the VPN’s parent company before committing. Providers often share data with their parent companies, and if that company is based somewhere sketchy privacy-wise, your data could be in for a rough ride.
Wrapping up on the best VPNs for privacy, let’s rank the providers to see which VPNs lead on no-logs guarantees, operate under the most privacy-friendly jurisdictions, have undergone independent audits, and whose parent companies aren’t beholden to major surveillance alliances.
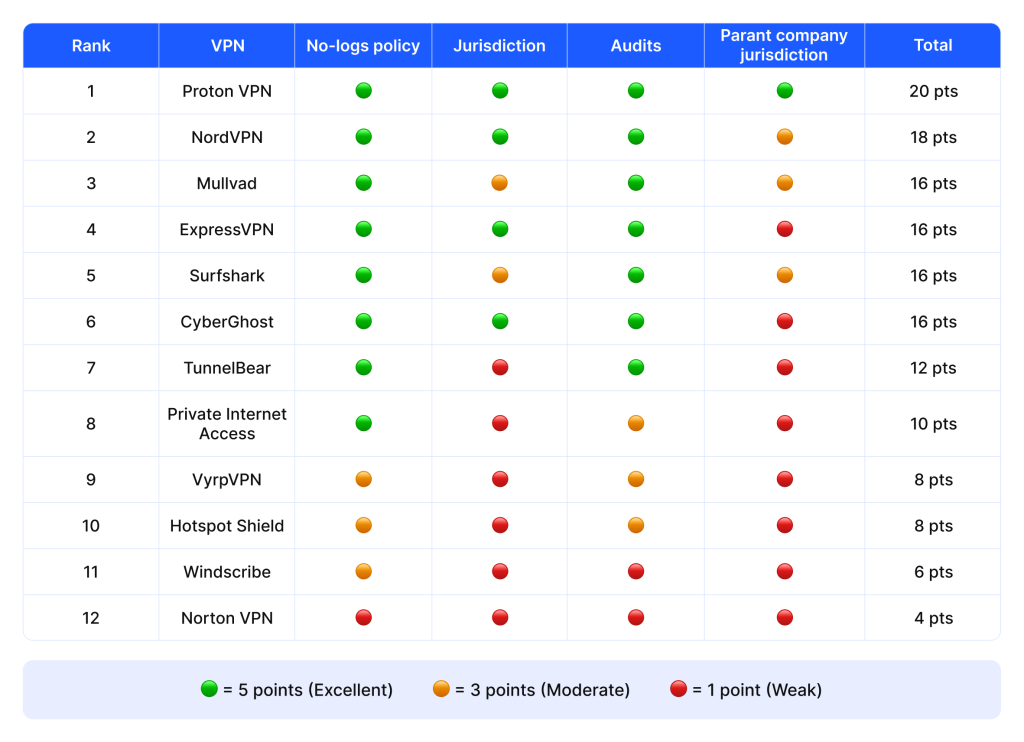
🔍 How to read this:
- No-logs policy: Do they truly keep zero identifiable logs (5), only minimal session metadata like bandwidth usage (3), or do they store more extensive logs (1)?
- Jurisdiction: Are they under privacy-friendly legal frameworks (5), mixed (3), or Five Eyes (1)?
- Audits: Have they been audited multiple times (5), once (3), or not at all (1)?
- Parent jurisdiction: Does their parent company reside in a privacy-friendly state (5), mixed (3), or Five Eyes (1)?
VPN Anonymity Explained: Can a VPN Hide You Online?
VPNs are excellent for bypassing content restrictions and hiding your browsing activity. However—as this article has shown—they won’t make you vanish from the internet. From timestamps to browser fingerprinting, there are still plenty of ways to deanonymize you.
That said, there is no need to lose heart. Unless you’re up to something criminal, choosing a provider with a verified no-logs policy, privacy-friendly headquarters, and built-in leak protection will make you nearly impossible to identify in most cases. If you’re on the intelligence services’ radar, though, no VPN is going to be a magic cloak.
What about alternative tools? There is Tor and proxies, but they each have their own trade-offs. Tor wins on pure anonymity but is noticeably slower and more complex. Proxies are fast and okay for quick, app-specific IP masking—but offer no encryption. And VPNs, while not offering complete anonymity, strike the golden mean between privacy, security, and speed—keeping you private and ensuring your data stays yours, provided you choose wisely.
Wrapping up, here is your quick privacy checklist—follow these tips to get the most out of your VPN:
- Choose an independently audited VPN with a strict no-logs policy
- Prefer VPNs outside the Eyes alliances and double-check their parent company’s jurisdiction
- Enable IPv6, DNS, and WebRTC leak blocking
- Use the kill switch to avoid accidental IP exposure.
- Keep your app up to date
- Avoid unencrypted HTTP sites
- Practice good hygiene: unique usernames, strong passwords, and 2FA wherever possible.
Hope you enjoyed this article—feel free to share if you found it helpful!
And stay tuned: in our next article, we’ll test VPN performance to see which services deserve the crown for speed and stability.