Tor vs VPN: The Tor Project, best known for Tor Browser and Orbot, has quietly rolled out its beta VPN. Is it a game-changer that will reshape the VPN industry or just another ordinary tool? I tried the app myself and am now ready to explain what Tor VPN is, how it differs from traditional VPNs and Tor Browser, and what it could mean for privacy-minded users and the VPN market.
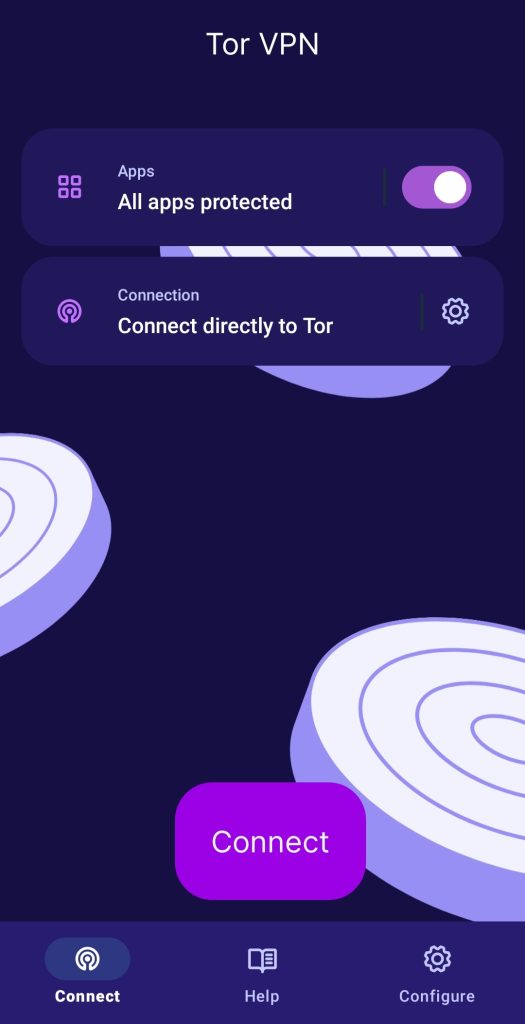
Tor vs. VPN—Understanding the Differences
One of the most common questions around Tor is “Is Tor a VPN?” Well, not exactly. Both encrypt traffic to hide your activity and location, but they do it differently. So how is Tor different from a VPN?
- Tor (short for “The Onion Router”) routes internet traffic through multiple layers (hence the onion reference) using a global network of volunteer-operated servers.
- VPNs (virtual private networks) route traffic through a single—unless you use a multi-hop feature—private server operated by the VPN provider.
As you can see, the main difference between Tor and a VPN is how they route traffic. Multiple layers give Tor stronger anonymity, while shorter paths make VPNs faster—a classic Tor vs. VPN trade-off.
💡 Pro tip: Do you need a VPN for Tor?
Most of the time, no. Tor is a self-sufficient tool that ensures strong privacy and doesn’t need a separate VPN setup. However, you can use Tor over a VPN connection in certain cases—for example, if Tor is blocked in your region; this can hide Tor usage from your ISP.
The Technology Behind Tor’s Privacy
But let’s dig a bit deeper: what is onion routing, and how does Tor work? Onion routing is the main idea behind the Tor network: unlike how VPNs work, your data gets wrapped in multiple encryption layers and sent through a chain of relays. Each relay peels one layer and forwards the packet, so no single node can link the sender to the destination, giving Tor a significant anonymity advantage over traditional VPNs.
What Is Tor VPN, and How Does It Work?
Tor VPN is a beta, Android-only app that uses the Tor protocol and routes device traffic through the Tor network instead of a commercial VPN provider’s servers. While Tor Browser provides only browser-level protection, Tor VPN lets you pick which apps use Tor, with per-app circuits and exit IPs so each app can appear to come from a different route.
In short, Tor VPN brings onion routing out of the browser and into other apps while staying true to the Tor Project’s mission: promoting anonymity to fight censorship and surveillance.
Speaking of the tech under the hood, Tor VPN is built on Arti (Tor’s modern Rust implementation)—modern, memory-safe code with easier maintenance compared with older C clients. This emphasis on memory safety isn’t just technical preference; it directly impacts security by preventing common vulnerabilities like buffer overflows and use-after-free bugs that could compromise user privacy. Developers building privacy-critical software like Tor typically rely on oss code security tools during development to catch such vulnerabilities before they reach users. Tor VPN includes most standard privacy features. Here are the key ones:
- Split tunneling with per-app circuits & exit IPs: Choose which apps use Tor and which use the regular connection. The app can build separate Tor circuits for different apps so that each app appears with a different IP address.
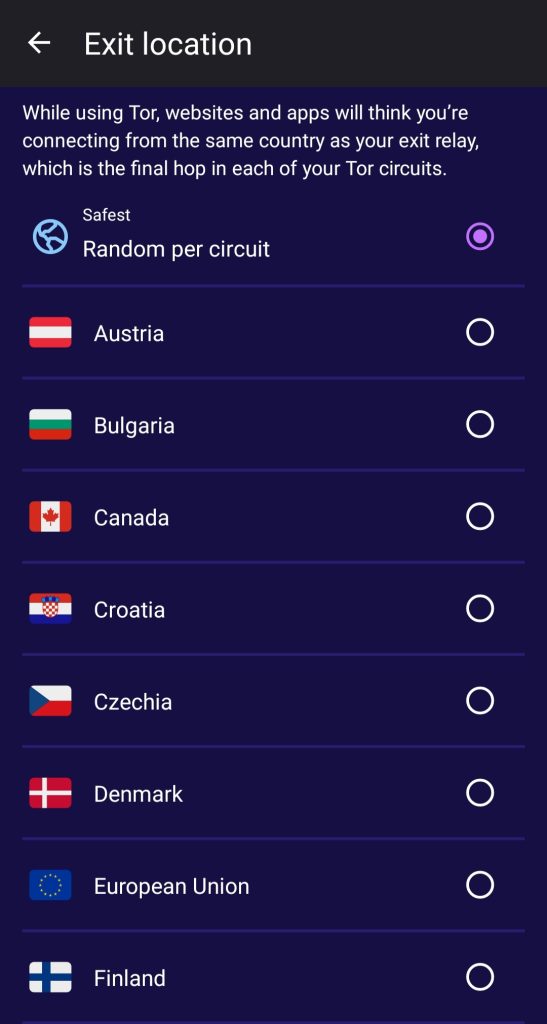
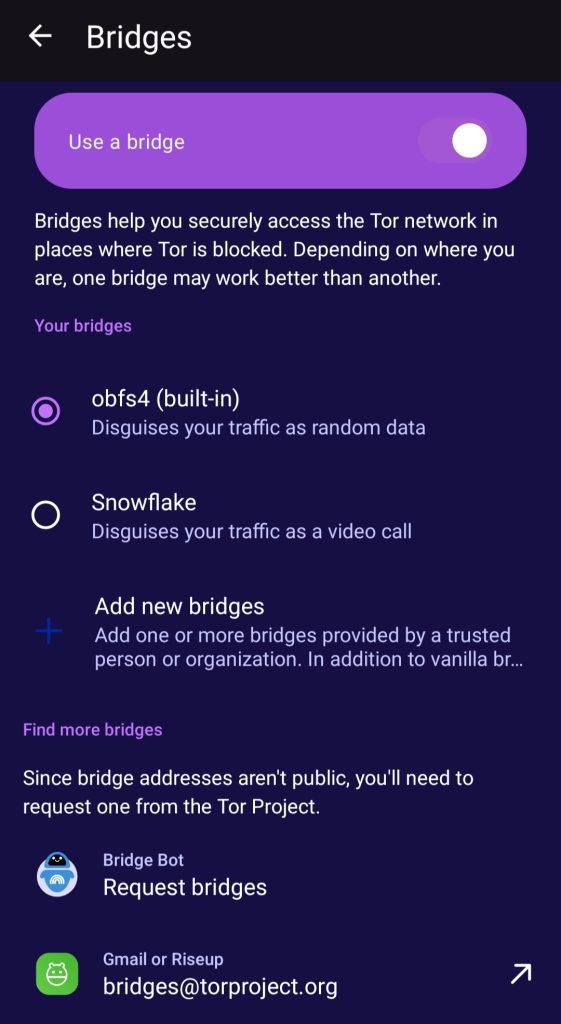
- Censorship circumvention: Tor VPN supports bridges to reach the Tor network from places where Tor is blocked. You can select one of the built-in bridges or request more via Tor’s Telegram bot. Here’s what the built-in bridges can do:
- obfs4: Obfuscates traffic to look like random data and prevent censors from finding bridges.
- Snowflake: Routes your traffic through proxies, masking it to appear as a video call.
- Kill switch: Blocks apps from connecting to the internet if the Tor network can’t be reached.
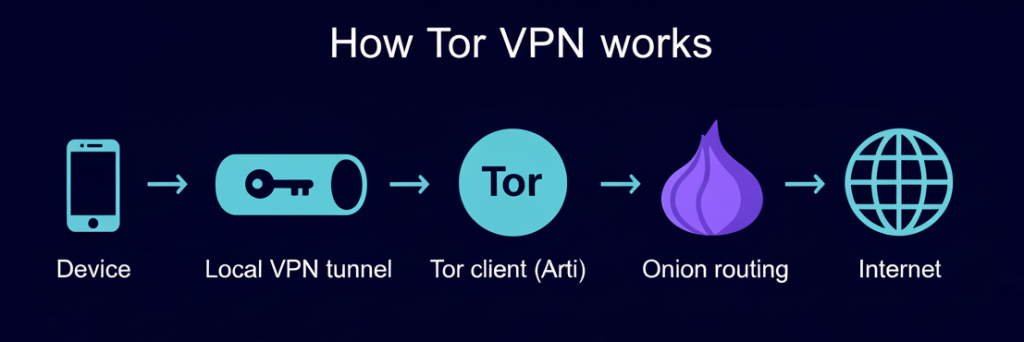
How Tor VPN works:
The app creates a local VPN tunnel on the device and forwards the captured traffic into the Tor client (Arti). Arti builds multi-hop onion circuits and sends traffic through volunteer relays, so the device gets Tor’s layered encryption anonymity model at the OS level and can route non-browser apps through Tor—useful for messaging apps or any app you want to isolate—while leaving latency-sensitive apps off Tor for performance.
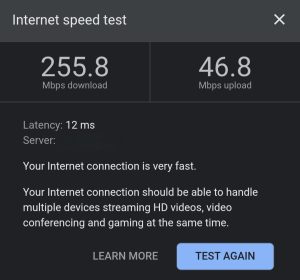
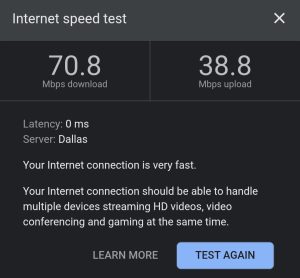
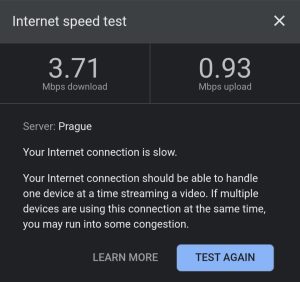
Even though the app is a beta, it already seems solid in use, and you get all the core features you need for private browsing. The one—but huge—downside for me is speed: due to its onion design, Tor VPN reduces speeds to around 3–4 Mbps even on a high-speed connection. Here’s the comparison of my connection speed without VPN vs. Proton VPN vs. Tor VPN:
| No VPN | Proton VPN | Tor VPN |
|---|---|---|
 |  |  |
Except for the speed, Tor VPN checks all the boxes for a truly private tool. If you also want to try it for yourself, the Tor Project is actively asking for testers and feedback. Remember that the build is early-stage and explicitly not yet suitable for highly sensitive activities. If that’s not the case, and you want to be among the first to test-drive the app, you can get it via the Google Play Store.
Privacy, Security, and Limitations
Tor’s onion routing gives you a strong anonymity advantage, but it doesn’t magically solve Tor’s challenges. Here’s what Tor VPN actually gives you—and what it doesn’t:
| Upsides | Limitations |
|---|---|
| ▪️ Censorship circumvention: Built-in bridges can help you bypass blocked networks to reach the open web. | ▪️ Speed and latency: Multi-hop onion routing is much slower than modern VPN protocols such as WireGuard. |
| ▪️ Split tunneling with per-app circuits: Isolates traffic per app and reduces linkability between different apps on the same device. | ▪️ Feature gap vs. commercial VPNs: No desktop clients and no streaming optimizations—Tor VPN is not a drop-in replacement for everyday VPN use cases. |
| ▪️ Decentralized model: Unlike a single-provider VPN, Tor’s multi-hop relays mean no single operator can see both ends of a connection. | ▪️ Learning curve: Per-app circuits add power but also complexity—non-technical users may misconfigure settings and unintentionally weaken privacy. |
| ▪️ Free and open source: Like other Tor projects, Tor VPN is open source, transparent, and free to use. |
Is it worth it? It depends on your use case. If your priority is anonymity and censorship circumvention, Tor’s beta is interesting and worth testing. If you need reliable streaming, low-latency gaming, or multi-platform support, a commercial VPN is still a better choice.
💡 Quick tip: Types of VPN Explained: How Each Works and Which Is Best for You
Impact on the VPN Industry and the Future of Privacy Tools
For years, Tor and VPNs were treated as alternatives: VPNs for speed and convenience, and Tor for distributed anonymity. Tor stepping into the VPN territory shows those lines can blur and may shake that established balance. Here are the key takeaways:
- Privacy pressure: Tor shipping a device-level VPN raises the bar for commercial players. Expect more questions about logging policies and audits.
- Technical hybrids: We’ll likely see experiments that mix onion routing with faster tunneling protocols—a middle ground between Tor’s model and traditional VPNs.
- Market segmentation: Tools will split more clearly into “privacy-first for mainstream use” and “anonymity for high-risk cases.”
The VPN market trends show a growing need for privacy tools, but many users want them for streaming and gaming—tasks that aren’t Tor’s strong suits. Tor VPN won’t displace commercial providers soon, but it may improve user education and push VPNs to become more transparent and secure.
A New Chapter for Tor and Online Privacy
Tor VPN is built on the Tor Project’s strengths and brings Tor’s anonymity model to apps outside the browser. But it also carries the usual Tor vs. VPN trade-offs—notably lower speed and higher latency—and that can be decisive if you prioritize performance over privacy.
I’ve tested the app for a few days, and here’s my verdict: Tor VPN is great for privacy (advanced split-tunneling with random exit nodes and bridges for obfuscation are excellent), but if you need low latency or cross-platform convenience, a commercial VPN still wins. In any case, Tor VPN is an important experiment that could nudge the future of privacy tools toward more transparency and stronger security—which is better for all of us.
FAQs
Is Tor a VPN?
No—Tor itself is not a VPN; it’s an anonymity network that uses onion routing. However, Tor VPN, a freshly released Android beta, is a system-level VPN app that uses the Tor network.
How does onion routing work?
Onion routing wraps your data in multiple encryption layers and sends it through volunteer relays. Each relay removes one layer, so no single node sees both origin and destination. That’s the core of Tor’s anonymity model.
Does Tor Browser have a VPN?
No. Tor Browser routes browser traffic through the Tor network. Tor VPN is a separate, system-level Android app.
Should I use a VPN with Tor?
Using Tor over a VPN is generally unnecessary for most users and can sometimes harm anonymity. Tor’s own VPN reduces the need for a third-party VPN in many cases.
How secure is Tor VPN?
Tor is known for its strong security and distributed anonymity. Tor VPN is open source and features bridges for censorship circumvention and split tunneling with per-app circuits, but it’s a beta and explicitly experimental, so it may be risky for sensitive use cases.