Not so long ago, privacy online meant clearing browser history and hoping no one noticed. Today, it’s IDs, biometrics, facial scans, real name logins, age checks, and increasingly—digital identity verification that follows you from state services to banking to logging into a food delivery app. As sad as it may be, the internet is no longer the anonymous free-roam space many of us grew up with.
At the same time, VPNs have quietly become our handy privacy tools. Not just for streaming and bypassing geoblocks, but for something much simpler: returning that feeling that you can Google and browse unobserved without someone peeking over your shoulder.

We ran a survey to see how people actually use VPNs—not assumptions, not industry predictions, but real habits. Some use them for work. Many for bypassing blocks. But a significant chunk turns them on with one purpose in mind: to avoid feeling like their online life is being recorded, sorted, and filed.
This article digs into that intersection—where digital ID rollouts meet VPN blowback, which countries lead the charge in adoption of national digital ID systems, why this trend is accelerating, what people fear, and how privacy tools are evolving as our online identities become harder to separate from who we are offline.
Privacy Expectations vs. New Verification Realities
There’s a mismatch between how many of us expect the internet to behave—private, pseudonymous, a place for side quests—and what regulators and platforms now demand: verified identity for safety, commerce, and law. And that cultural tug-of-war is the context for every headline about mandatory digital ID. But what is digital ID to begin with? In most cases, it’s a credential or an app (sometimes issued by a government, sometimes by a private provider) that proves who you are online or confirms a specific fact about you—like your age.
The whole cycle of online age assurance evolution has passed before our eyes: the first checks were humble—a checkbox and a shrug. Next came self-attestation (“I am over 18”), then card gates and paywalls. When platforms needed stronger proof, they added photo ID uploads and manual verification. Today we’re seeing the next leap: cryptographic wallets, government-backed eID apps, AI-based tools—more and more online age verification methods are being tested at scale. Each step traded friction for assurance—and privacy for certainty.
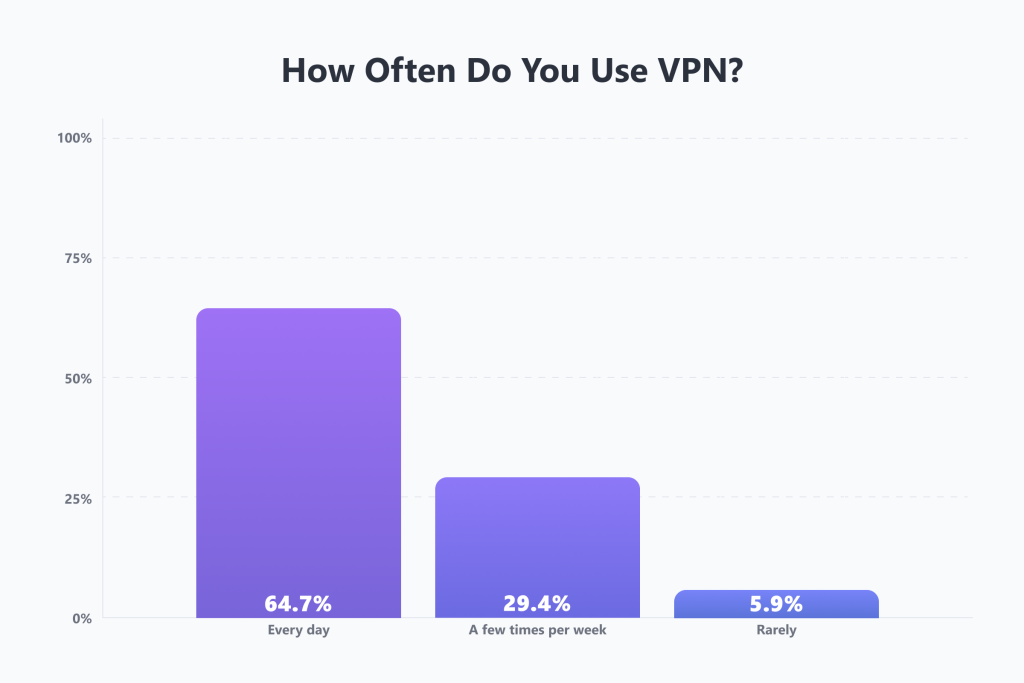
And this isn’t hypothetical. Two-thirds of countries now have foundational digital ID systems that support some form of digital identity verification or authentication for services—a sign that national digital ID programs are not niche experiments but a mainstream trend. And this trend doesn’t go unanswered. Whenever verification becomes headline news, VPN interest spikes: when the UK introduced new age check rules this summer, there was a sudden surge in VPN downloads, with five VPN apps breaking into the App Store’s top 10.The same pattern repeats in other markets as well. You’ll be surprised by how many people use VPNs: data shows that more than a fifth of all internet users have them now, and current VPN usage statistics suggest that this number will only climb. And this isn’t just an occasional tool for travel—it’s a daily habit. Our own research shows that roughly two in three users rely on their VPN every single day, with another 29% using it a few times a week.
So what’s actually behind these stats, why do people use VPNs increasingly more these days, and can they really help against digital ID systems?
Why People Install VPNs—and What They Actually Do
Let’s slightly shift from feelings and policies to behavior and software: what people reach for when they feel exposed, and whether that tool actually does what they think.
What drives installs?
Sharp headlines trigger a reflex: feeling vulnerable creates a desire for control, and we predictably turn to the most visible privacy tool we know—a VPN. That move might be emotion-driven, but it’s still rational and often helpful.
That said, while impulsive reactions generate spikes, the VPN market grows for a handful of more prosaic reasons too: work (remote access to a company network), streaming (watching georestricted shows), privacy (hiding your IP from ISPs or ad trackers), bypassing local blocks, and so on.
What the data says
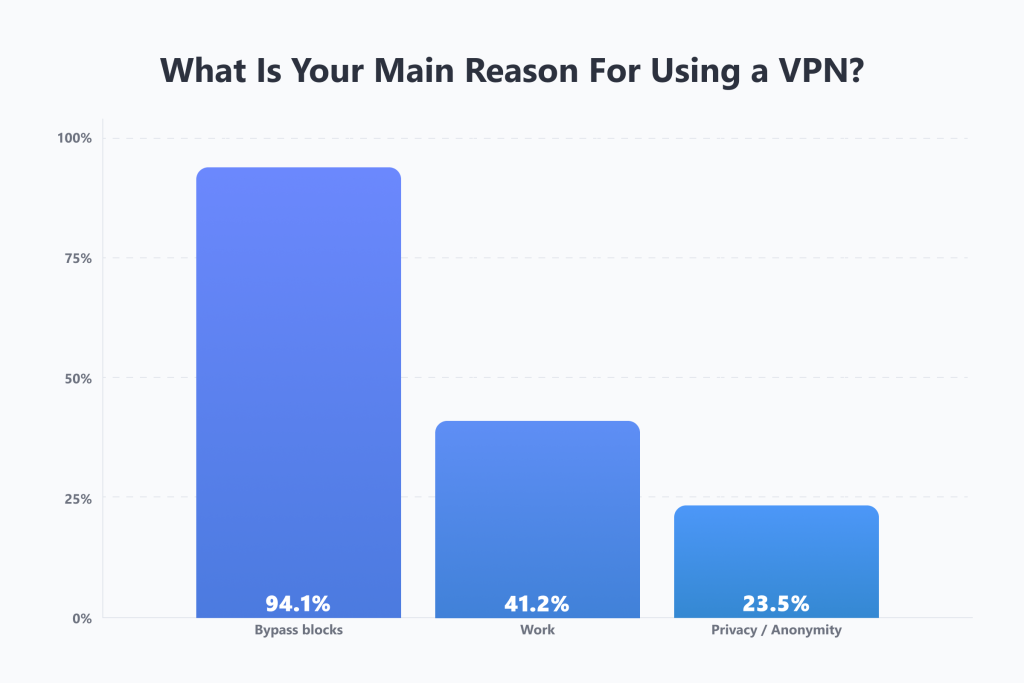
Our data backs this up. In a recent survey of our users, we found that a staggering 94% of respondents named “bypassing blocks” as a main reason for usage, while 41% pointed to work-related requirements, and roughly every fourth uses a VPN for privacy.
Most interestingly, the very definition of “privacy” is shifting. While the majority of users (over three in four) traditionally named hiding an IP as the main reason, when we asked what respondents actually meant by the term, almost half specifically mentioned avoiding government surveillance—significantly more than those who just want to avoid ISP or platform tracking. This confirms that for a large chunk of users, a VPN is no longer just a utility for content; it is a shield against being watched.

What a VPN actually does
A VPN is a network-layer tool that creates an encrypted tunnel between your device and a VPN server. When it’s on, your ISP sees only an encrypted connection to the VPN provider, and websites see the VPN server’s IP rather than your home IP—which lets you appear to browse from another country.
💡 Quick tip: Types of VPN Explained: How Each Works and Which Is Best for You
What a VPN does notdo
When it comes to VPN and age verification, a VPN is not always a solution. It can hide where you are, not who you are. If you upload a passport photo, submit to a biometric match, or present an attestation from a digital wallet to a digital identity verification service, that record exists independently of your IP address. A VPN won’t remove it, and it won’t unlink the credential from whatever account you used to submit it.
What are the limits?
Platforms actively detect and block VPNs because they interfere with geopricing and fraud controls—with free services coming first as their server IPs get exposed sooner. But even if a VPN isn’t blocked, platforms can tie verification to payment methods, device IDs, or certified wallets—things a VPN doesn’t touch. In this case, using a VPN to trick an age gate will be pointless: you might bypass a geography check, but you’ll still hit the stronger verification wall soon after.
So what should I do?
VPNs are useful sidekicks, but treat them as just one layer of protection. If you want stronger privacy, use Tor—it’s better at origin hiding but slower. On the account level, use pseudonymous names where allowed, strong passwords, and multi-factor authentication.
Country Snapshots: How Digital ID and Age Assurance Rollouts Shape Behavior
So what are the real stories behind the headlines? Let’s try to figure out what people actually do on the ground when national digital ID or age-check headlines break.
United Kingdom
When the mandatory age checks under the UK’s Online Safety Act hit the news, people reacted immediately. Many outlets reported “explosive growth” of VPN downloads across app stores, and major providers saw dramatic signup percentage increases just a few minutes after the new rules took effect.
Another hot topic is the UK’s digital ID rollout. The government has recently announced plans to make the digital ID mandatory in the UK, at the very least for right-to-work checks. When will the digital ID be mandatory in the UK? The GOV.UK Wallet (the official digital ID name) is expected to be adopted by the end of the Parliament, which means no later than 2029. However, Brits don’t take this initiative lightly—over a million signatures in support of the digital ID petition in the UK against the introduction of digital ID cards on the first day speaks for itself.
European Union
The EU is moving toward a unified digital identity—and fast. Under the eIDAS 2.0 regulation, every member state must offer a Digital Identity Wallet (EUDI) to its citizens by December 2026. While usage is technically voluntary for citizens, it will become mandatory for service providers in banking, transport, and telecommunications to accept it—effectively making it the default key to modern life.
Simultaneously, the Digital Services Act (DSA) is tightening the net on online anonymity. With new guidelines for protecting minors taking full effect in July 2025, major platforms are being pushed to implement “effective” online age verification methods. The reaction on the ground has been swift: several EU countries instantly saw the surges in VPN use and faced protests against biometric age verification.
USA
Unlike the EU’s centralized vision, the U.S. digital ID and age assurance approach is fragmented and state-driven. States like Louisiana, Utah, and Virginia led the first wave of mandatory age verification laws for adult content, requiring users to upload government IDs to access certain sites. The trend accelerated in late 2024 and throughout 2025, with states like Missouri joining the list. The user response was immediate and predictable: when Missouri’s law took effect in November 2025, local searches for VPNs quadrupled in a matter of days.
Meanwhile, adoption of mobile driver’s licenses (mDLs)—the U.S. version of digital IDs—is growing. While this type of digital ID in the USA is not mandatory, the Transportation Security Administration (TSA) is now increasingly accepting them at select airports.
Australia
Australia’s Social Media Minimum Age amendment, which requires social media platforms and search engines to verify users’ age to prevent under-16s from running into harmful content, took effect in December 2025, is predicted to boost VPN downloads, and already makes waves in the Aussie internet. Media report serious concerns from young content creators, with some of them forced to leave Australia to avoid the upcoming ban.
The plans for digital ID in Australia make no less noise than its British counterpart. While the system is promised to be voluntary at launch, people still ask questions about whether Australia’s digital ID rollout will be secure and about potential scope expansion in the future.
China
China’s digital ID (or Cyberspace ID) rollout is a different animal. The system is state-led and hit millions of downloads within weeks courtesy of state channels pushing rapid adoption as a convenience and compliance tool for accessing services. Civic pushback has been muted (for obvious reasons), but rights groups and NGOs raised early warnings about expression and surveillance risks. With VPN use in China remaining constrained by law and aggressive blocking, attempts to evade state systems carry real legal and operational risks that most citizens weigh seriously.
Other countries
- India: India’s digital ID (Aadhaar) is already deeply integrated. Verifications amount to hundreds of millions per month, so people here treat it as routine, and no big VPN download surges have been reported.
- Estonia: Estonia’s digital identity verification system has long been part of daily life for citizens. E-ID is widely used for banking, business, taxes, and signatures; it’s largely trusted and hasn’t faced any widespread resistance.
- Brazil: Brazil’s Gov.br platform is everywhere: hundreds of millions of registered interactions and deep service integration mean people tend to accept the system as a convenience rather than react with a mass VPN rush.
- South Korea: South Korea’s digital ID systems rolled out fast and broadly. Public reaction has been pragmatic, with fast uptake for payments and public services and no reported VPN use spikes.
While policy announcements can produce short-term spikes in VPN downloads and searches, the longer-term response depends on local incentives and design—and this pattern repeats across countries with digital ID programs. If a digital ID is positioned and built as a convenient service gateway with strong privacy protection, people tend to treat it as utility. If it feels invasive, expect resistance—and VPN interest—in waves.
How Can We Protect Our Privacy?
The rules and decisions made by platforms and regulators today will decide which verification model will dominate the market: a privacy-respecting one, driven by discretion and care for personal data, or a convenience-first, identity-centralizing one that every criminal and ad network dreams of. And while the verification storm is imminent, we can still make small choices to mitigate its effects. Here’s what works:

- Pick attribute-based attestations. If you have a choice, always prefer separate, cryptographically verifiable attestations that prove only one fact about you, like your age, instead of sharing passport or driver’s license scans—tokens are cheap to check and expensive to abuse.
- Check retention policies. Before you upload anything, check for how long the platform will keep your data. If the answer is vague or indefinite, press the company for specifics, request deletion after verification, or walk away. Because if it’s no longer necessary, why keep it?
- Prefer providers with transparency. Look for a digital identity verification service that publishes simple transparency reports or verification metrics (how many verifications they do, how long they keep data). If a company won’t say, treat that as a red flag. Public transparency is the easiest proxy for a vendor that’s less likely to quietly monetize your data.
- Avoid biometrics when you can. Don’t volunteer face scans or voiceprints unless there’s a clear legal requirement or no other available option. One thing about biometrics is once they leak, you can’t change them. If a service requires face matching, ask how long they keep the image and insist on deletion.
- Use privacy-friendly alternatives. When a website asks for a credit card check or phone bills for age confirmation, prefer a wallet token or a prepaid payment method—prepaid cards can reduce the link between your spending and your identity.
- Keep a separate account for risky services. Use a separate email and account with minimal personal links where possible. Don’t tie everything to your main address.
- Use a reputable VPN sensibly. If a service’s verification is region-based, a VPN can help. Pick paid, audited providers (free ones can monetize traffic or even sell data), enable a kill switch, and don’t rely on a VPN as a sole privacy solution.
💡 Quick tip: How to Set Up a VPN at Home (Beginner-Friendly Guide)
- Ask for deletion—and keep proof. When you delete an account or request data removal, take screenshots and save confirmation emails. If a company refuses, you’ll want that paper trail for a regulator complaint.
Even if it may seem insignificant now, it’s small moves, repeated across millions of users, that count and that force better verification design with minimal privacy losses.
What the Future Holds: Key Trends to Watch
We can monitor tendencies, create graphs, and make forecasts, but the future of verification isn’t set in stone. So let’s try to peek into the crystal ball and predict what we could expect in the near term.
- Selective disclosure will go mainstream (or not). Expect more pilots with cryptographic attribute (“over-18”) tokens. Crypto protection sounds nice, but a lot will depend on UX. If it’s clunky, simpler verification methods will win.
- Consolidation vs. fragmentation battle. Watch for a few big digital identity verification companies to try to dominate verification markets. Regulators that don’t act will create monopolies; regulators that insist on open standards will keep the market competitive and less risky.
- Privacy-preserving tech will gain momentum. Zero-knowledge proofs, verifiable credentials, and digital identity verification solutions with selective disclosure will be at the center of attention, but widespread adoption depends on whether their use will be seamless to users and “just work.”
- Areas of application will multiply. Once social media and adult content are on board, expect more sector-specific checks, with gambling, fintech, and healthcare among the first that come to mind.
- Civil society will shape the rulebook. Petitions, lawsuits, and NGO campaigns already work and will continue to tilt policy—and often more than tech hype does.
- VPN demand will continue to be a real-time thermometer. Human psychology isn’t likely to change soon. As a result, app store spikes will continue when policy changes hit headlines. Remote work and ongoing regional blocks are now part of everyday life. These are key reasons people already use VPNs, and download numbers will keep growing.
How to Keep Your Privacy When the Internet Starts Asking for ID
Digital ID and mandatory age checks are no longer theory—they’re the inevitable reality. And this reality is still messy: verification can protect kids and reduce fraud, but it also risks concentrating identity, exposing sensitive data, and locking out people who lack documents. At the same time, VPNs have become a reflexive response. They offer some relief from region-based checks, but they cannot help when services require passport photos or wallet attestations.
So what should you take away? Verification design is still evolving in many regions. How people respond may influence how these systems take shape. To protect your privacy, use attribute-only attestations when possible. Check how long sites retain your data, avoid biometrics unless necessary, and use a reputable VPN. In the end, the choices we make today can help keep verification systems privacy-respecting in the future.
FAQs
Can a VPN make me anonymous under digital ID systems?
No. VPNs hide your network location and encrypt traffic, but they don’t erase the identity you hand over (ID scans, selfies, wallet attestations). They’re a privacy layer, not a replacement for credentials.
Can a VPN bypass age verification online?
It can for geography-only checks. However, if a system asks for ID, biometrics, or accredited attestations, it won’t be of much help.
Which countries have digital ID systems?
Currently, two-thirds of countries have foundational ID systems, but approaches vary: some countries, like China, push broad, state-led identity systems; others, like the EU, UK, and Australia, introduce voluntary projects with targeted mandatory uses.
Will a digital ID make VPNs pointless?
No. People will still use VPNs for work, protection on public Wi-Fi, and geoflexibility. However, they won’t help bypass services that require a digital ID.