Keyloggers are classes of spyware that trace every key stroke on the device and record sensitive information like passwords or personal messages. It normally records information for malicious use such as identity theft or fraud.
Types of Keyloggers:
- Hardware Keyloggers: Physical devices that plug into a computer for capturing keystrokes.
- Software Keyloggers: Programs installed on an operating system to monitor the keystrokes and log them.
Keystroke logging can be installed by phishing emails, malicious downloading, infected attachments, and/or attaching a hardware device to a computer.

Signs of a Keylogger Infection
- Slow Performance: Noticeable lag in system speed; Delays in typing or mouse movements; Apps take longer to open, or the system freezes more often.
- Unusual Data Usage: Unexpected spikes in internet usage, possibly due to keyloggers sending captured data.
- Strange Files or Apps: Unknown files or programs you didn’t install, which could be a keylogger or related malware.
Means for Keylogger Detection
Detecting a keylogger on your computer means checking unauthorized software tracking your keystrokes. Here it is:
For Windows Users:
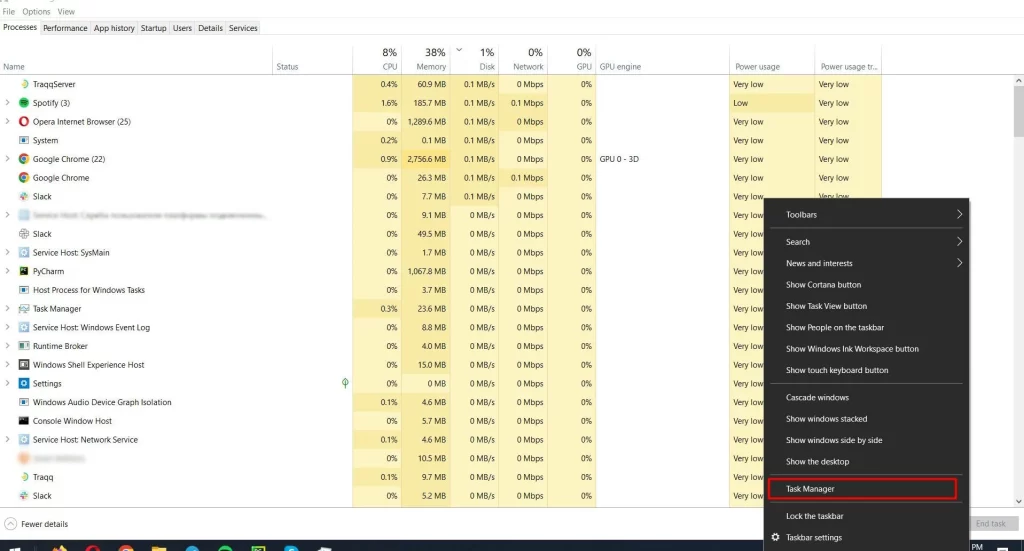
Use the Task Manager:
- Open Task Manager by right-clicking the taskbar and then selecting “Task Manager.” Expand to “More Details” to show all running processes.
- Scroll through the list and flag unknown or suspicious processes. Right-click to select and “End Task” to kill the process.
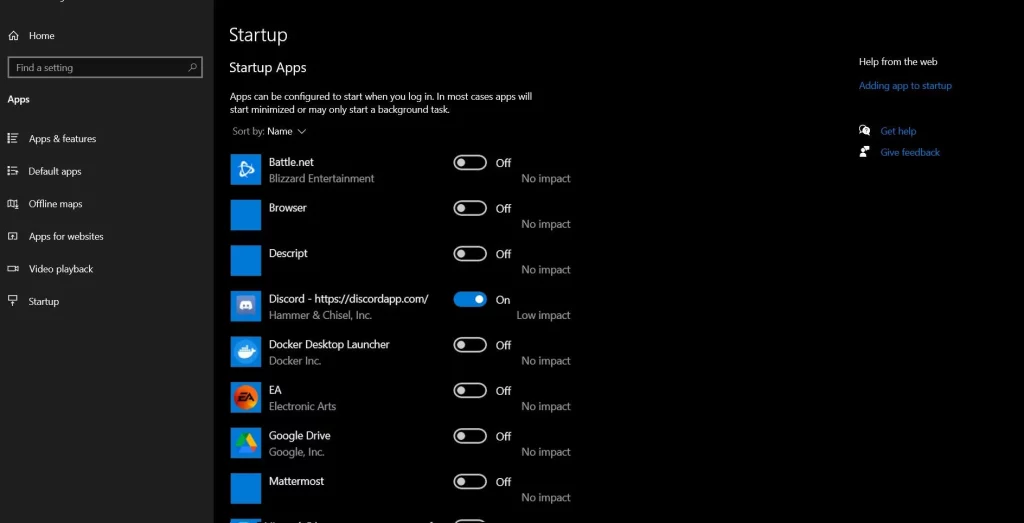
- Check out what’s in the “Startup” tab, which controls which programs auto-start with your computer and disable unnecessary or unfamiliar entries.
- Review Installed Programs: Go into Control Panel, then “Programs” > “Programs and Features.”.
Look for anything suspicious or unknown in the list of installed programs. Anomalies can be researched online and removed if they are potentially bad.
For Mac Users:
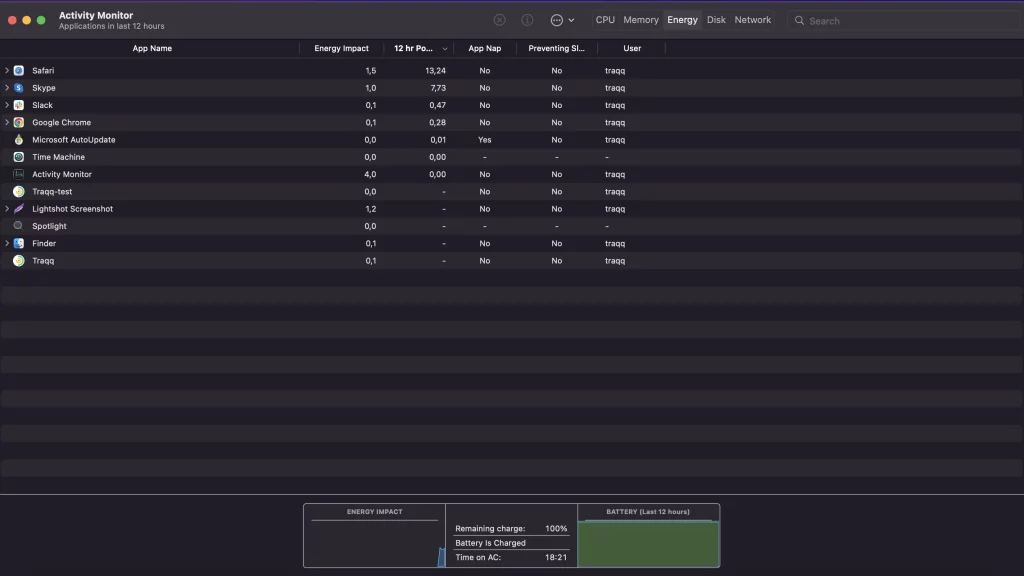
Use Activity Monitor:
- Launch the Activity Monitor utility inside Applications, Utilities.
- Check all the running processes for anything that looks unusual. Look up any suspicious items online and if necessary close the process by selecting it and clicking the “X” button.
Suspicious Programs Identification:
On the two systems, watch the programs with weird names and higher usage of resources on unreasonable grounds, and unknown applications; these can be the keyloggers.
Checking for Unusual System or Browser Changes:
- System Settings: Search for things you never changed. This can include any new programs starting automatically, changed browser homepages or even search engines, and added toolbars.
- Browser Extensions: Look through your browser extensions or add-ins. Remove any you didn’t install, or those that seem superfluous.
- Look for keyloggers by monitoring your computer for strange activity and investigate unknown programs or processes through a name search online to confirm if they are safe.
How to Remove Keyloggers
Uninstalling Suspicious Programs
For Windows:
- Open Control Panel by pressing the Windows key, typing “control panel,” and pressing Enter.
- Go to Programs > Programs and Features to view installed software.
- Look for unfamiliar or suspicious programs.
- Right-click the program and select Uninstall, then follow the steps to remove it.
For Mac:
- Open Finder and navigate to the Applications folder.
- Scroll through the list for any suspicious apps you didn’t install.
- Drag the unwanted app to the Trash, or right-click it and select Move to Trash.
- Right-click the Trash icon and choose Empty Trash to permanently delete the app.
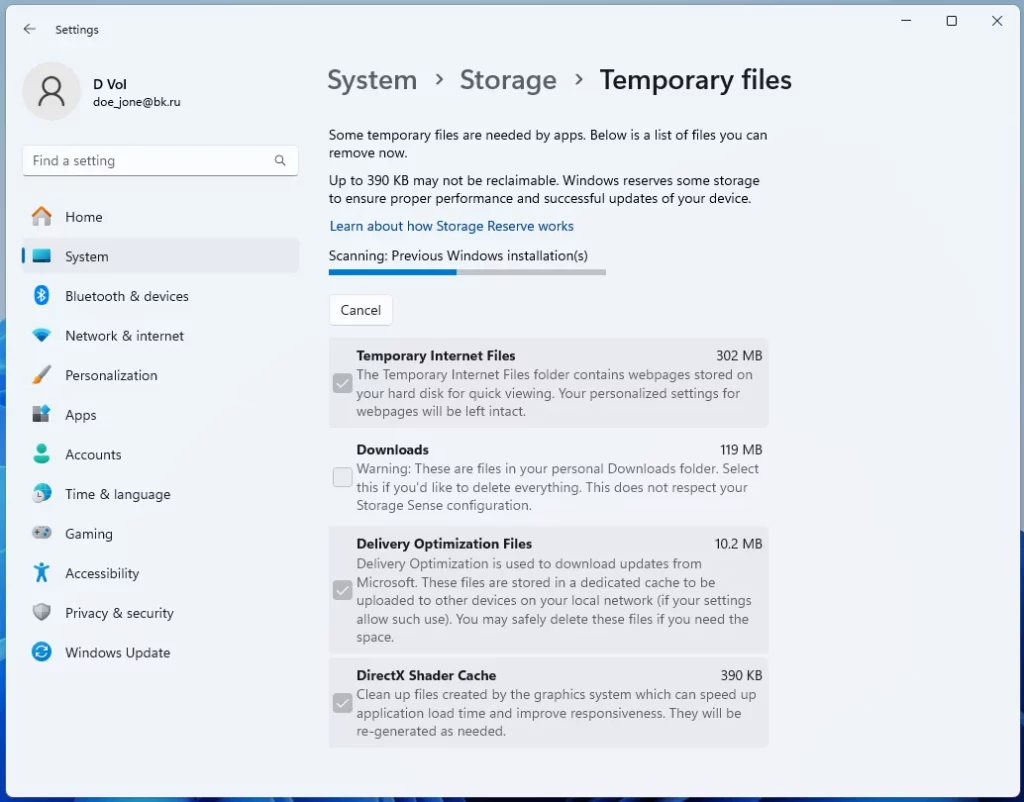
Clearing Temporary Files
For Windows:
- Open Settings through the Start menu by clicking the gear icon.
- Go to System >> Storage.
- Under the section Local Disk, click Temporary files.
- Choose to select file types to delete and click Remove files; doing this clears temporary data where keyloggers might hide.
For Mac:
- Open Finder.
- Then go to the Go menu option and select Go to Folder.
- Input
~/Library/Cachesand press Enter. - Delete unimportant or suspicious files with caution and never delete anything important to your system.
Afterwards, always run an antivirus to ensure that all the keyloggers and bad files are deleted.
Resetting Your Device to Remove Keyloggers
The final solution for the removal of keyloggers is resetting your device; you should back up data that might be important for you to avoid loss.
Backing Up Data:
- For Computers/Laptops: an external hard drive or cloud storage.
- For Android/iOS: back up your contacts, photos, and apps using Google Drive, iCloud, or external storage.
How to Reset Devices
Windows:
- Open Settings from the Start menu.
- Under Update & Security, select Recovery.
- Under Reset this PC, select Get started.
- Select Remove everything and follow the prompts to reset.
MacOS:
- Restart your Mac. Immediately hold the Command + R keys. This will open up Recovery Mode.
- Open Disk Utility and erase your disk.
- Go back to Recovery Mode and select Reinstall macOS, following the on-screen instructions until it’s complete.
Android:
- Settings > System > Reset options.
- Select Erase all data (factory reset) and follow the prompts.
iOS:
- Open Settings > General > Reset.
- Tap Erase All Content and Settings and confirm.
After that, install only trusted software to keep it secure. Actually, this process resets your device to factory settings, hence getting rid of keyloggers and other malware.
Protecting Your Device from Keylogger Attacks
Keeping your device safe from keyloggers includes good habits of security and protection software.
Update Your System and Software
Make sure that your operating system and applications are up-to-date, patching those vulnerabilities through which keyloggers will try to get in.
Use Strong Passwords
Establish complex, unique passwords for each account, mixing letters, numbers, and symbols. For convenience and security, use a password manager.
Run anti-virus and anti-malware software in real time that would find and block keyloggers. Regular scanning of the system and its updates.
Stay Informed and Educated
Understanding how keyloggers work will help to take care of your device efficiently, always stay updated about the recent trends in cybersecurity.
By following the above steps, you reduce the chances of attacks by keyloggers and hence keep your data secure.
Regular scanning with updated tools offers a better way of surfacing threats and protecting your personal data. Always keep your software current for better protection against new risks.
You can keep yourself safe from such mischievous activities by being vigilant and using tools like Outbyte AVarmor for effective detection and removal of keyloggers.
FAQs
1. What is a keylogger?
A keylogger is some form of program or device that constantly records every keystroke done on a computer to grab sensitive data.
2. Do all keyloggers be considered malignant?
No, keyloggers may serve legitimate uses-for example, to monitor staff productivity. Nonetheless, there is great employment of it for malicious purposes by cyber hoodlums.
3. Can keyloggers be picked up by anti-virus programs?
Yes, practically all reliable antivirus programs pick and clear keyloggers.
4. How can I avoid keyloggers infecting my device?
Install strong security software, avoid downloading files from untrusted sources, and regularly update your system.