Introduction
There are many types of VPN that can be used for different jobs—from simple privacy protection and remote access to connecting offices or even self-hosting servers. Knowing how to apply them helps you choose the right solution for home use, business networks, or advanced setups.
This guide explains the different types of VPN, their pros and cons, and where VPN protocols like OpenVPN, WireGuard, PPTP, L2TP, and IKEv2 fit in.
Main Types of VPN Connections
One great thing about VPNs is their multi-purpose nature—you can use them for a number of various tasks. But what are the different types of VPN? Below are quick descriptions to help you pick the right one for your use case.
Personal VPN
This is what most people think of when they hear “VPN”: your regular VPN app on a phone, laptop, or router that creates a tunnel to a server. Tunnels can be full (encrypting all traffic) or split (allowing only some apps through the VPN).
- Use cases: device protection, access to streaming libraries and blocked websites, bypassing censorship, getting better prices on services, split tunneling for mixed use.
- How it works: the client connects to a VPN server and opens an encrypted tunnel that routes and protects your traffic.
Who it’s for: home users.
Remote access VPN
Remote access VPNs let users connect to a private network from anywhere. Work remotely or travel often? A remote access VPN helps you securely reach your office or personal network from anywhere.
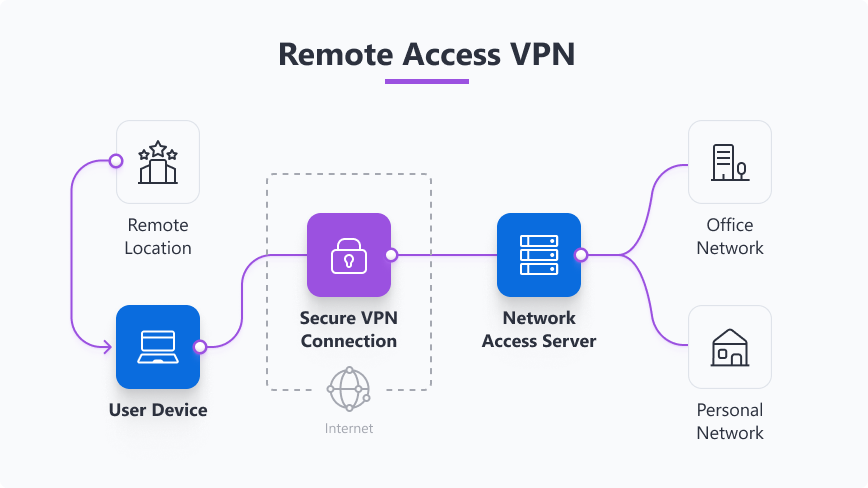
- Use cases: work-from-home access, personal network remote access.
- How it works: similarly to the personal VPN, the client on your device authenticates and creates an encrypted tunnel to a VPN server.
Who it’s for: everyone—from beginners to pros.
Site-to-site VPN
Site-to-site VPNs link two or more networks together. This type of VPN is commonly used by businesses to securely connect a branch office to headquarters.
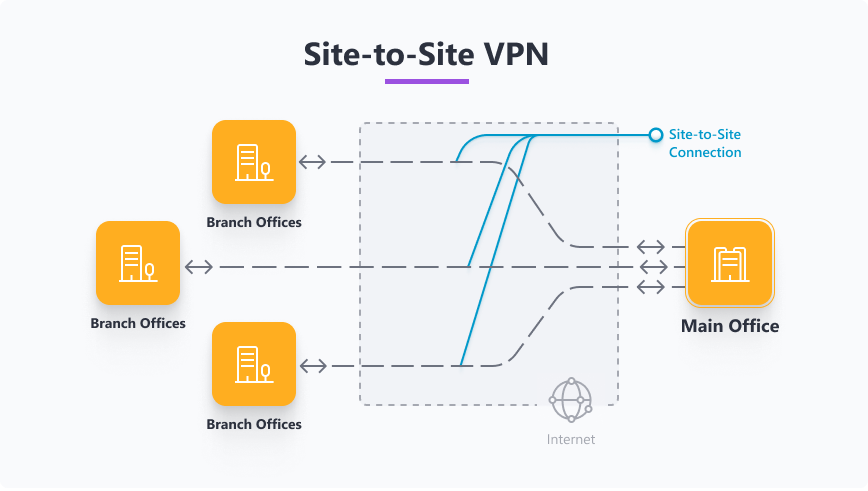
- Use cases: connecting office networks, merging cloud and on-premises networks.
- How it works: routers or dedicated VPN gateways establish tunnels between networks.
Who it’s for: companies and organizations with multiple locations.
Cloud VPN
Cloud VPNs are “all-in-one” solutions delivered as a service (VPNaaS) that are very easy for organizations to deploy because they offload the setup, scaling, and maintenance to a provider or cloud platform.
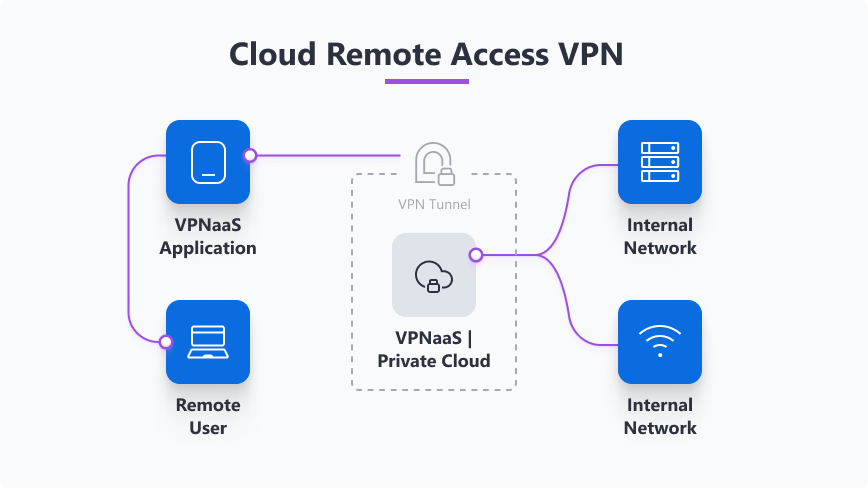
- Use cases: connecting distributed teams, quick site-to-cloud links, and organizations that want a managed remote access option without running their own gateways.
- How it works: a cloud provider runs VPN gateways, and you connect clients or branch routers to those gateways.
Who it’s for: businesses and teams that need scalable, low-maintenance connectivity.
SSL VPN
SSL VPNs provide access to remote networks using the same SSL/TLS technology that secures websites, either via a portal or a tunnel. Portal is web-based, meaning you don’t need a client app and can quickly access internal web resources. Tunnel is like a regular VPN app (using SSL/TLS) that is useful when you need RDP, file sharing, or broader remote access beyond just web apps.
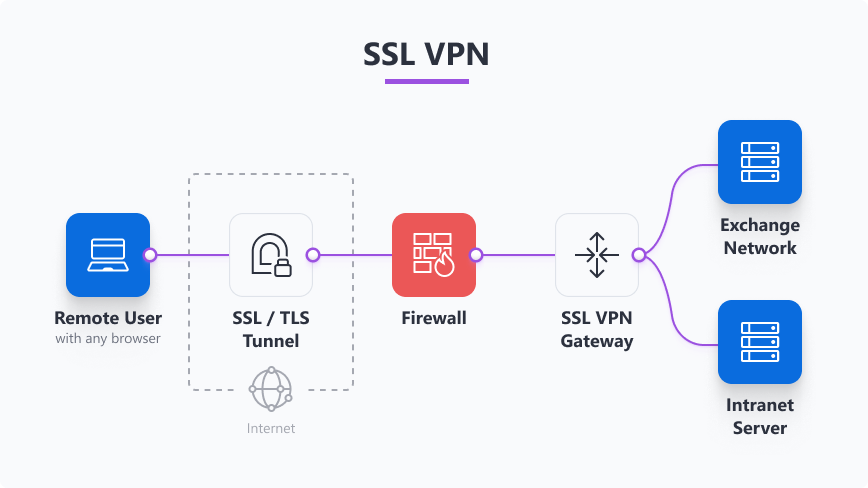
- Use cases: browser-based access to internal apps, remote desktop, web portals.
- How it works: secure web connections (HTTPS-like) tunnel specific applications or sessions.
Who it’s for: organizations prioritizing simplicity and app-level access.
VPN Protocols Explained
Let’s start this section with a simple question: “What are VPN protocols?” VPN protocols are the rules and methods that make VPNs work: they define how devices authenticate, encrypt data, and send traffic through tunnels. That choice affects performance, device battery life, how well the connection survives network changes, and whether a firewall will let your traffic through.
In practice, this means different protocols behave differently on real networks. Some VPNs optimize for low latency or fast throughput, while others focus on maintaining reliability when your device switches networks. Some use UDP (typically faster but more likely to be blocked by restrictive networks); others can run over TCP or port 443 to look like normal HTTPS traffic and bypass firewalls.
Platform and deployment matter: many operating systems include built-in support for a few protocols, while full-featured clients add more options. Routers and corporate gateways often support only certain protocols, so your choice depends on what the endpoints accept.
Operational details also matter: protocols differ in how they authenticate (using certificates vs. keys), how they handle NAT/firewall traversal, and what ports they use. These differences affect setup steps on routers and servers, and they’re why some VPNs offer a protocol selector in the app—to match your network or device.
Rule of thumb: use a modern, well-supported protocol by default and switch only if you have a specific reason—for compatibility, to bypass blocked ports, or need a special routing. Test a couple of options for speed and stability, and keep your client and server software updated for timely security fixes.
Types of VPN Protocols
Some protocols, such as PPTP and L2TP, are older and still supported on many legacy devices. Newer ones — like WireGuard, modern OpenVPN builds, and IKEv2 — focus on speed, security, and mobile resilience. So, let’s take a closer look at these different types of VPN protocols.
PPTP
Very old and easy to set up. The PPTP VPN protocol appeared in the mid-1990s, and Microsoft promoted it widely, integrating it into many legacy operating systems and older routers. Because it’s simple, you can still find a VPN with PPTP on ancient devices and in some legacy corporate gear. Certain obsolete setups also keep running PPTP VPN server instances—but PPTP encryption is weak, and the protocol has many known vulnerabilities. Avoid it for anything that needs real privacy.
L2TP/IPsec
The L2TP VPN protocol itself came later and, when paired with IPsec, became a common standard in the late 1990s–2000s for adding encryption to VPN tunnels. It’s widely supported across desktop and mobile OSes and on many routers, which made it a popular default for vendors for years. It’s more secure than PPTP but can be slower due to double encapsulation and sometimes gets blocked by strict firewalls, so it’s usually used where compatibility matters but performance isn’t critical.
OpenVPN
OpenVPN arrived in the early 2000s and became the go-to open-source choice for secure, configurable VPNs. It’s used everywhere: consumer VPN services, self-hosted OpenVPN server setups, business appliances, and many routers. OpenVPN offers strong encryption and flexibility (it supports TCP/UDP and custom ports), but it usually needs a client or config file—so it’s slightly more hands-on.
IKEv2/IPsec
The IKEv2 VPN protocol (paired with IPsec) became standardized in the mid-2000s and is valued for resilience—it handles network changes (Wi-Fi ⇄ mobile data) very well. That makes it a common choice for mobile devices and corporate remote access. It’s secure and fast on phones and tablets and is often built into OSes, which simplifies deployment for mobile-first users or managed environments.
WireGuard
The WireGuard VPN protocol is the newcomer that gained traction in the late 2010s and made its way into the Linux kernel around 2020. It was designed for simplicity and speed using modern cryptography. Because of that, many providers now offer WireGuard, and people run WireGuard VPN server instances on VPSes and home gear. It’s excellent for home users and self-hosted setups where performance and a small codebase matter.
So which VPN protocol is the best? Let’s quickly compare them side-by-side.
VPN protocols: Comparison
| Protocol | Pros | Cons | Typical use |
|---|---|---|---|
| PPTP | ✅ Very easy to set up ✅ Built into many legacy OSes and routers | ❌ Weak, outdated encryption ❌ Many known vulnerabilities | Legacy devices, compatibility-only scenarios |
| L2TP | ✅ Broad platform support ✅ More secure than PPTP | ❌ Double encapsulation can slow speeds ❌ Sometimes blocked by firewalls | Older devices and vendor-default setups where compatibility matters |
| OpenVPN | ✅ Strong encryption ✅ Highly configurable | ❌ Heavier setup ❌ Can be slower than modern options | Self-hosted servers, business appliances, broad compatibility needs |
| IKEv2 | ✅ Excellent mobile resilience (reconnects fast) ✅ Often built into OSes | ❌ Less flexible for complex routing ❌ Certificate/SA management can add overhead | Mobile-first users, corporate remote access, managed environments |
| WireGuard | ✅ Very fast ✅ Strong encryption ✅ Easy to audit and maintain | ❌ Newer (but widely adopted) ❌ Some enterprise features still evolving | Home users, VPS/self-hosted servers, performance-focused setups |
Which VPN Type Should You Choose?
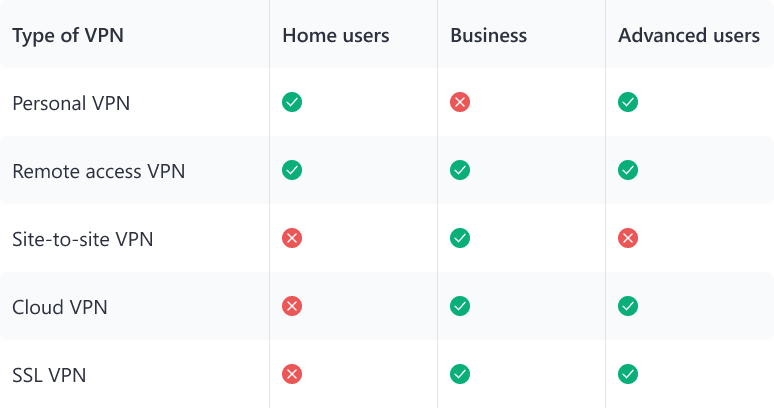
Your choice of the type and protocol should first of all be determined by your needs. Different types of VPN connections solve different problems—privacy, site-to-site networking, or remote access—so focus first on what you need to do, then choose a protocol that supports that use case.
Home users
If you need a VPN for remote access to have a link with your home network while you’re away or just a simple VPN client for privacy, use a no-log provider that offers ready-made apps and supports WireGuard and OpenVPN—both top the list of VPN security protocols. Choose WireGuard if you want speed and simplicity, and OpenVPN if you need a battle-tested protocol with broader device compatibility.
If you prefer protecting every device, set the VPN on your router so smart TVs and consoles are covered without individual installs.
Quick tip: Check out our article on how to set up a VPN at home for more info.
Businesses
Companies usually need reliable, permanent site-to-site VPN connections between locations or SSL VPNs for secure remote employee access. If you want fast rollout and reduced gateway maintenance, cloud VPNs are a common choice for modern, distributed teams.
Evaluate the WireGuard vs. OpenVPN tradeoffs for performance and manageability, and weigh cloud-managed convenience against running your own appliances before making the final decision.
Advanced users
If you want full control—custom routing, a self-hosted server, or private cloud access—you can run your own OpenVPN or WireGuard server on a VPS, NAS, or Raspberry Pi. WireGuard is great for performance-focused, low-overhead setups. OpenVPN offers more configurability and wider support.
If you have specific compatibility needs, use L2TP or IKEv2, but avoid PPTP unless you’re dealing with truly legacy gear.
Different types of VPN: Quick comparison
| Type of VPN | VPN protocols | Recommended use | Security | Speed | Ease of setup |
|---|---|---|---|---|---|
| Personal VPN | ✅ WireGuard ✅ OpenVPN ✅ IKEv2 ✅ L2TP ✅ PPTP | Protect phones, PCs, tablets | ➞ WireGuard, OpenVPN, IKEv2—high ➞ L2TP—medium ➞ PPTP—low | ➞ WireGuard—excellent ➞ OpenVPN, IKEv2, PPTP—good ➞ L2TP —moderate | Easy |
| Remote access VPN | ✅ WireGuard ✅ OpenVPN ✅ IKEv2 ✅ L2TP ✅ PPTP | Remote workers, travel access | ➞ WireGuard, OpenVPN, IKEv2—high ➞ L2TP—medium ➞ PPTP—low | ➞ WireGuard—excellent ➞ OpenVPN, IKEv2, PPTP—good ➞ L2TP—moderate | Easy (via client) to moderate (manual) |
| Site-to-site VPN | ✅ WireGuard ✅ OpenVPN ✅ IKEv2 ✅ L2TP | Connect branch offices, permanent network links | ➞ WireGuard, OpenVPN, IKEv2—high ➞ L2TP—medium | ➞ WireGuard—excellent ➞ OpenVPN, IKEv2—good ➞ L2TP—moderate | Moderate to advanced, depending on gateway config |
| Cloud VPN | ✅ WireGuard ✅ OpenVPN ✅ IKEv2 | Scalable remote access for teams, cloud links | High | ➞ WireGuard—excellent ➞ OpenVPN, IKEv2—good | Very easy (managed service) |
| SSL VPN | ✅ SSL/TLS | App- or browser-level access to internal resources | High | Good | Easy to moderate, depending on appliance |
Different Types of VPN: Explained
While it’s hard to tell exactly how many types of VPN exist, I tried to cover the main types of VPN connections in this article. Personal and remote access VPNs are best for everyday privacy and home users; site-to-site and SSL VPNs will better fit businesses that need custom setups; and cloud VPNs add a scalable option for teams and organizations that want fast rollout without running appliances.
Protocols like WireGuard and OpenVPN are the sensible choices for secure, fast connections. IKEv2 is a reasonable option for mobile-first users and corporate remote access. At the same time, while L2TP and PPTP are still supported by legacy gear and can still be implemented for specific needs, L2TP is dated and generally less secure and slower than modern protocols, and PPTP is now considered obsolete and insecure.
Understanding the differences helps you pick the right mix: simple protection at home, resilient mobile access, or full network-to-network security.
Did you like the article? Let others know—share it on your socials!
FAQs
What are the different types of VPN protocols?
Common VPN protocols include PPTP, L2TP, OpenVPN, WireGuard, and IKEv2. They differ in speed, security, and compatibility—WireGuard and OpenVPN are the most recommended today.
Which VPN protocol is the most secure?
Security depends on configuration, but modern protocols (WireGuard, OpenVPN, and IKEv2) are considered secure when implemented correctly. Avoid PPTP for sensitive data, as it’s long outdated and has known security vulnerabilities.
Is WireGuard better than OpenVPN?
WireGuard is usually faster and simpler to audit, but OpenVPN remains highly configurable and compatible with many legacy setups. For most home and modern business use, WireGuard is an excellent choice. You can pick OpenVPN if you need wider compatibility or have specific legacy needs.