Introduction
VPNs are the king of globalization. They go further than cheap international flights and even foreign cuisine spots around the corner. They allow you to surf the internet from almost any part of the world without getting off the sofa.
VPNs have significantly eased our lives by opening up access to blocked or geo-restricted content. They also help bypass firewalls, protect our data and privacy while browsing, and even troubleshoot connection issues in some cases. But with so many players in the market, how do you pick the right one? Well, to answer this question, we’ll compare 12 select VPN services based on security, privacy, and performance.

In this article, you’ll get VPNs explained in simple terms, including how they work and what features matter most. We’ll also help you decide which one deserves the title of best VPN in 2025 for security. Intrigued yet? Let’s get to it!
How VPNs Work: The Basics
This may come as a surprise, but your internet provider knows whatever you do online without a VPN. They see most of your internet activity and log the domains you visit—yes, even in incognito mode.
They also track how long you spend on those sites, monitor your data usage, and record your general browsing habits.
Even if they can’t read the exact pages on HTTPS sites, they can still see which websites you access.
This happens through DNS queries and Server Name Indication (SNI) information.
Then there are website administrators who can see your IP address, browser details, and sometimes your approximate location. How do they see it? They can use cookies and other tracking methods—all to monitor your actions on their sites. And if you thought clearing cookies would keep you private—far from it. Browser fingerprinting might still follow you around.
Finally, while you’re visiting non-HTTPS resources, your data remains unencrypted, allowing others—or worse, malicious actors—to intercept it.
I believe you’ve already caught my drift. Using a VPN saves you this headache by protecting your connection and hiding your activity from anyone but yourself. Well, unless there’s someone watching the screen behind your back.
What Happens When You Connect
So, what happens behind the scenes when you hit that Connect button in your VPN app? To put it simply, the VPN client encrypts the data from your computer and sends it through a secure tunnel. This process masks your IP address and makes websites think you’re connecting from the VPN server’s location, not your own.
Let’s visualize the process:
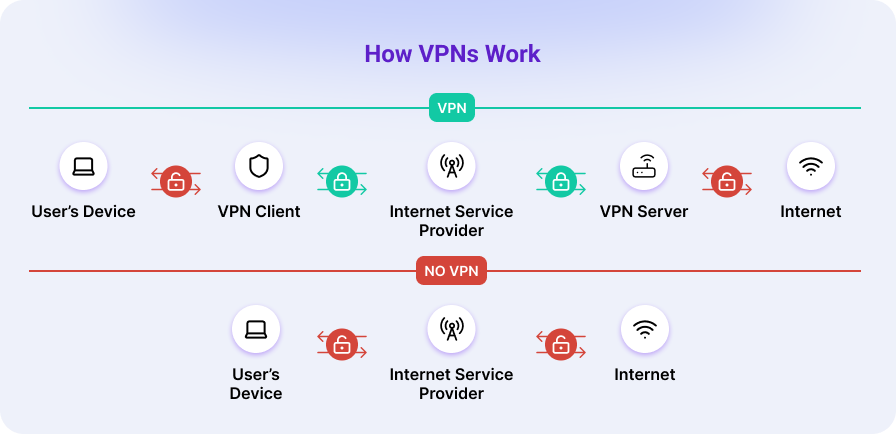
- Connection: Once you launch the app and hit Connect, your device handles all its traffic off to the VPN client, which establishes a tunnel (secure link) with a VPN server.
- Encryption: Next, it scrambles the data sent from your device from plaintext (readable data) into ciphertext—an unreadable and indecipherable (or nearly indecipherable) mumbo-jumbo.
- Data routing: Once encrypted, the VPN sends your data through the tunnel via your ISP—who sees only ciphertext—straight to the VPN server.
- Decryption: Finally, at the other end, the VPN server decrypts (or unscrambles) the data so the website or service you’re connecting to can read it. The VPN server replaces your real IP address with its own and only decrypts the part protected by the VPN tunnel before forwarding your request to the website.
Skip the VPN client and tunnel, and your device’s requests travel through your ISP in plain view. ISPs (and anyone watching them) can see the sites you visit and your real IP address, making your browsing far less private.
Encryption
Cryptography—specifically, encryption—is the secret sauce inside VPNs that helps keep your data private. It transforms your readable data into a jumble of scrambled code that only those with the right key can decipher, ensuring that your data remains confidential and secure—whether you’re sending an email, browsing the web, or shopping online.
There are two main flavors here:
- Symmetric encryption: Uses one key for both locking and unlocking your data.
- Asymmetric encryption: It uses a pair of keys (public and private) primarily during the key exchange process and ensures that even if someone intercepts one key, the encryption still protects your data.
Now, what are the key VPN encryption types? Basically, all VPN (or tunneling) protocols make use of one of the two encryption standards:
- AES (Advanced Encryption Standard): Military-grade, block cipher encryption introduced in 2001, the most popular of the two and adopted by the U.S. government, among others.
- ChaCha20: Introduced in 2014, ChaCha20 is a stream cipher that offers a very high level of security. It’s generally faster, performs better in embedded systems and on mobile platforms, and many modern protocols—like WireGuard and other proprietary ones—use it as their main encryption method.
VPN protocols explained
A VPN protocol defines the rules for encrypting and transmitting your data. It works by encapsulation, wrapping data packets within other packets to help them sneak through network tunnels undetected.
Not all protocols are the same, and like most things in life, you can’t have it all. Some protocols are faster and offer better performance on mobile devices, while others are more secure and reliable. So, let’s finally name them:
OpenVPN
Created by James Yonan as a side project due to mistrust of internet providers from countries with “deeply untrustworthy security practices” back in 2001, OpenVPN has quickly become the most popular, secure, and widely supported VPN protocol. It uses the industry gold standard encryption—AES-256—and still lives by the founder’s rule.

What’s more, OpenVPN is open-source, and security experts around the world regularly audit its code—leaving little room for doubt about its security level.
WireGuard
Introduced in 2018, WireGuard comes from ZX2C4 (also known as Jason A. Donenfeld among non-geeks). The main idea behind WireGuard was to craft a protocol that would be lighter and faster than IPsec (bear with me, we’ll get to it soon) and more performant than OpenVPN. The developers achieved this by “trimming the fat” from the codebase and using ChaCha20 encryption, which offers high-speed performance—especially on mobile devices that don’t support hardware acceleration for AES.
At the same time, it’s also open-source and doesn’t compromise on security, which makes WireGuard not only faster than OpenVPN but equally as safe, and that’s why its adoption is rapidly growing.
IKEv2/IPsec
Many experts refer to IKEv2 (Internet Key Exchange version 2) as IKEv2/IPsec, since it only works in combination with another VPN protocol—IPsec (Internet Protocol Security), which debuted in the 1990s. IKEv2 followed in the mid-2000s, and despite its more complex setup and bulkier codebase compared to OpenVPN and WireGuard, many still regard it as one of the best VPN protocols for mobile devices. It quickly reconnects when switching between Wi-Fi and cellular data while delivering top-tier security, making it a favorite for those glued to their phones.
That said, it can be trickier to set up in certain environments, and not all providers include it as an option.
Finally, there are proprietary protocols (more on them later in the article) that build on existing ones and are unique to each VPN provider, so you won’t find them outside those ecosystems.
Tunneling protocols comparison chart
| Protocol | Type | Popularity | Encryption strength | Speed | Compatibility | Use case | Pros/cons |
|---|---|---|---|---|---|---|---|
| OpenVPN | Open-source | Very high | Strong (AES-256) | Moderate | Cross-platform | General use, privacy-focused |
|
| WireGuard | Open-source | Rapidly growing | Strong (ChaCha20) | Very fast | Cross-platform | High-speed needs, mobile users, streaming, gaming |
|
| IKEv2/IPsec | Open standard | High | Strong (AES-256) | Fast | Mobile-friendly | Mobile devices, unstable networks |
|
| NordLynx | Proprietary (NordVPN) | High | Strong (ChaCha20) | Very fast | Cross-platform | High-speed needs, privacy-focused |
|
| Lightway | Proprietary (ExpressVPN) | High | Strong (AES-256) | Very fast | Cross-platform | Speed and simplicity |
|
| Stealth | Proprietary (various VPNs) | Moderate | Strong (AES-256) | Moderate | Cross-platform | Bypassing censorship, deep packet inspection (DPI) evasion |
|
| Chameleon | Proprietary (VyprVPN) | Moderate | Strong (AES-256) | Moderate | Cross-platform | Bypassing VPN blocks, maintaining speed |
|
| Hydra | Proprietary (Hotspot Shield) | Moderate | Strong (AES-256) | Very fast | Cross-platform | Streaming, gaming, high-speed browsing |
|
| Mimic | Proprietary (Norton) | Low | Strong (AES-256) | Moderate | Cross-platform | Bypassing DPI and VPN restrictions |
|
The Best VPNs in 2025: Feature-by-Feature Comparison
You may have already noticed that VPNs differ greatly in their design, offering a range of features and capabilities. The service you’ll use has to provide all the functions required for your use case. For example, you may prioritize speed over security or stability over performance, and vice versa.

That said, it’s about time we get to know our contenders. We’ve carefully picked 12 VPNs that consistently rank among the most popular and highly rated services in independent reviews and industry benchmarks. However, in this article, we’re focusing on security, remember? To get a full picture, make sure to check out our other articles, where we seek out the best VPN for privacy, touch on some unique VPN features, and test each VPN’s performance.
So, is your VPN really as safe as it claims, or might it be spilling secrets to Big Brother? Let’s take a closer look at what each VPN brings to the table.
| VPN service | Jurisdiction | No-logs policy | Servers & speed | Protocols | Cryptography | Kill switch | DNS leak protection | Split tunneling | Multi-hop | Obfuscation | RAM-only servers | Price |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Proton VPN | Switzerland | Yes, audited | 11k+ servers; 117 countries; up to 10 Gbps | OpenVPN, WireGuard, IKEv2, Stealth | AES-256/ChaCha20; 4096-bit RSA; HMAC-SHA384; FS: Yes | Yes | Yes | Yes | Yes | Yes (over the Stealth protocol) | No | Free (limited) Premium plans start at $4.49/month |
| NordVPN | Panama (owned by U.S.-based parent company) | Yes, audited | 7k+ servers; 118 countries; up to 10 Gbps | OpenVPN, IKEv2, NordLynx (proprietary), NordWhisper (proprietary) | AES-256/ChaCha20; 4096-bit DH; SHA384/SHA512; FS: Yes | Yes | Yes | Yes | Yes | Yes | Yes | From $3.09/month |
| ExpressVPN | British Virgin Islands (owned by UK-based parent company) | Yes, audited | 3k+ servers; 105 countries; up to 10 Gbps | OpenVPN, IKEv2, Lightway (proprietary) | AES-256/ChaCha20; 4096-bit RSA; SHA512; FS: Yes | Yes | Yes | Yes | No | Yes | Yes | From $4.99/month |
| Surfshark | The Netherlands (owned by U.S.-based parent company) | Yes, audited | 3.2k+ servers; 100 countries; up to 10 Gbps | OpenVPN, WireGuard, IKEv2 | AES-256/ChaCha20; 2048-bit RSA; SHA512; FS: Yes | Yes | Yes | Yes | Yes | Yes | Yes | From $1.99/month |
| CyberGhost | Romania (owned by U.S.-based parent company) | Yes, audited | 9k+ servers; 100 countries; up to 10 Gbps | OpenVPN, WireGuard,IKEv2 | AES-256/ChaCha20; RSA-4096; SHA256; FS: Yes | Yes | Yes | Yes (Android only) | No | No | Yes | From $2.03/month |
| VyprVPN | USA | Yes, audited | 700+; 63 countries | OpenVPN, WireGuard, IPsec (IKEv2), Chameleon (proprietary) | AES-256/ChaCha20; 2048-bit RSA; SHA256; FS: Yes | Yes | Yes | Yes | No | Yes (with the Chameleon protocol) | Yes | From $3/month |
| Private Internet Access (PIA) | USA (owned by U.S.-based parent company) | Yes, audited | 16k+ servers; 91 countries; up to 10 Gbps | OpenVPN, WireGuard, IPsec | AES-128/AES-256/ChaCha20; 4096-bit RSA; SHA1/SHA256; FS: Yes | Yes | Yes | Yes | Yes | Yes (via proxy) | Yes | From $1.98/month |
| Windscribe | Canada | Yes, not audited | 69 countries; up to 10 Gbps | OpenVPN, WireGuard, IKEv2, Stealth, WStunnel (proprietary) | AES-256/ChaCha20; 4096-bit RSA; SHA512; FS: Yes | No (uses Windscribe Firewall) | Yes | Yes | Yes | Yes (over the Stealth and WStunnel protocols) | Yes | Free (limited) Premium plans start at $1/location/month |
| TunnelBear | Canada (owned by U.S.-based parent company) | Yes, not audited | 8k+ servers; 46 countries | OpenVPN, WireGuard, IKEv2 | AES-256/ChaCha20; 2048–4096-bit DH; Varied; FS: Yes | Yes | Yes | Yes | No | Yes (GhostBear) | No | Free (limited) Premium plans start at $3.33/month |
| Hotspot Shield | USA | Yes, audited | 1.8k+ servers; 85 countries; up to 1 Gbps | WireGuard, IPsec (IKEv2), Hydra (proprietary) | AES-128/AES-256; 2048-bit RSA/ECDHE; N/A; FS: Yes | Yes | Yes | Yes | No | Yes (only with Hydra) | No | Free (limited) The premium plan starts at $6.66/month |
| Norton VPN | USA | Yes, audited | 2.8k+ servers; 29 countries | OpenVPN, WireGuard, IPsec (IKEv2), Mimic (proprietary) | AES-256/ChaCha20; Unknown; N/A; FS: No | Yes (excluding iOS) | Yes | Yes (excluding iOS and macOS) | No | Yes (Mimic only) | No | From $3.33/month |
| Mullvad VPN | Sweden | Yes, audited | 600+ servers; 49 countries; up to 10 Gbps | OpenVPN, WireGuard | AES-256/ChaCha20; 4096-bit DH; 4096-bit RSA w/ SHA512; FS: Yes | Yes | Yes | Yes | Yes | Yes | Yes | €5/month |
What does this comparison show us? Let’s break it down.
Jurisdiction

Jurisdiction matters because the country where a VPN operates determines how authorities can access and manage your data—like it or not, VPN providers must obey local data retention laws. If you plan to use a VPN, say, for streaming, and you’re okay with the government knowing where your provider operates from, there’s nothing to worry about. But if you were hoping for some private browsing, it’s worth looking into this matter first.
Proton VPN (Switzerland), NordVPN (Panama), ExpressVPN (British Virgin Islands), and CyberGhost (Romania) all operate from countries that don’t require companies to log or hand over user data and don’t participate in intelligence-sharing agreements—at least not to our knowledge. That said, keep an eye on Switzerland—since March 2025, it’s been weighing amendments to its surveillance laws that could require VPN providers to collect and store user data and cooperate with government requests. It’s far from certain these changes will pass, but consider yourself warned.
The Netherlands (Surfshark) and Sweden (Mullvad) also enforce strong data protection policies. However, the Netherlands belongs to the Nine Eyes alliance, and Sweden participates in the broader network known as the Fourteen Eyes. When it comes to VPNs explained in terms of jurisdiction and surveillance alliances, these distinctions can make a big difference.
And then there are the USA-based VyprVPN, PIA, Hotspot Shield, and Norton VPN, along with Windscribe and TunnelBear, headquartered in Canada, where surveillance laws can be even a bit more intrusive.
However, it’s not that simple…
Who owns your VPN?
VPN services are not as independent as you may think. Many are small clogs on bigger wheels. So, it’s wise to know which parent company owns your VPN to determine the true nature of their data storing policies.
For example, if a parent company operates under the jurisdiction of a Five, Nine, or Fourteen Eyes country, the government could still force it to hand over user data—even if the VPN provider says it’s based in the British Virgin Islands or Panama.
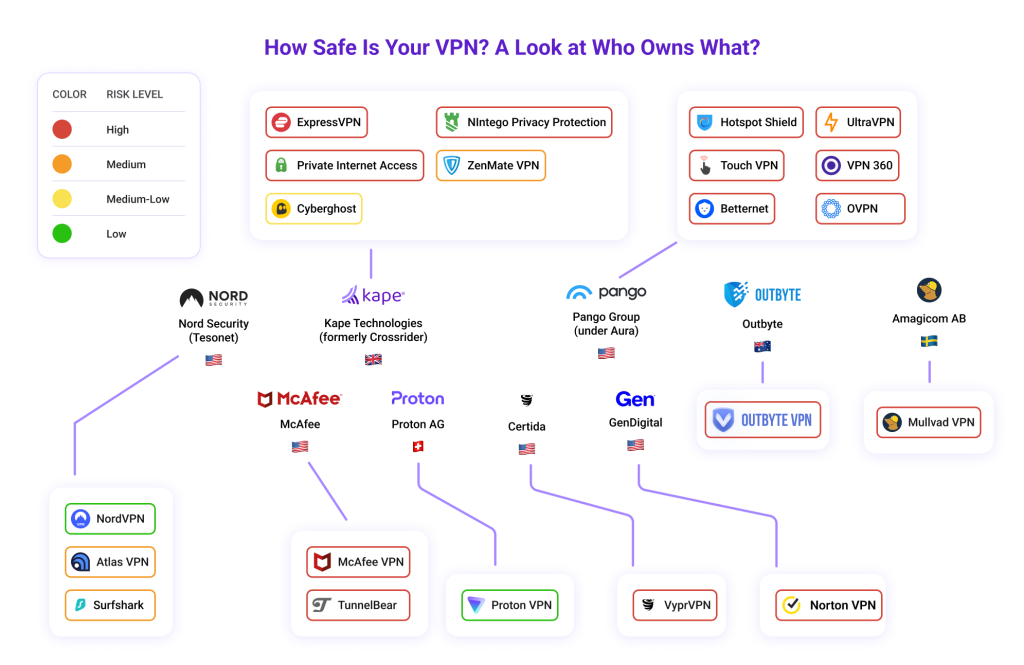
Only Windscribe and Mullvad on this list remain under the full ownership of their founders and employees. However, Proton VPN, VyprVPN, and Norton VPN do not share sister VPN services under their parent companies. TunnelBear also passes as one VPN service under McAfee since the McAfee VPN is a fork of TunnelBear.
No-logs policy
A strict no-logs policy means the VPN provider does not collect or store your online activity. So even if the government seizes a VPN server or requests data from the provider, there’s nothing to hand over. It’s quite important if you’re looking for a reliable VPN and privacy is not an empty word for you.
Most of our contenders—Proton VPN, NordVPN, ExpressVPN, Surfshark, CyberGhost, VyprVPN, PIA, Hotspot Shield, Norton VPN, and Mullvad—not only claim to have a strict no-logs policy (who doesn’t?), but go one step further and back it up with independent audits.
On the flip side, no independent firms have audited Windscribe and TunnelBear, which might make some of you wonder whether these providers are as forgetful as they claim. If keeping a low profile is your jam, a verified no-logs policy is a must.
For more detailed analysis, make sure to check out the next article in the series, where we’ll be sorting through the privacy features of VPNs, including their logging policies, and peeking into known incidents to confirm or refute their claims.
Number of servers & their speed
This one is quite obvious—the wider the server network, the more locations are available to you, and the higher the speed, the faster the connection. On top of that, having more servers usually means more capacity and thus, less congestion. Ever tried squeezing through a packed subway? Then you know what I mean.
NordVPN, Proton VPN, CyberGhost, Surfshark, ExpressVPN, and PIA have massive networks, giving you plenty of locations to choose from. Moreover, they all provide servers with 10 Gbps connections, and many experts currently regard these as the fastest available.
TunnelBear and Norton VPN may seem short in countries available, but they compensate for it with a solid server count. Mullvad, Hotspot Shield, Windscribe, and VyprVPN offer more server locations but have smaller networks.
But does less mean worse? Not necessarily. In short, while a larger network often means more choices and potential speed, quality and server placement are equally important.
VPN protocols
Almost all of the VPNs on our list support all three major protocols, which are (in case you forgot) OpenVPN, WireGuard, and IKEv2. The only exceptions are Hotspot Shield, which doesn’t support OpenVPN but compensates for it with its proprietary Hydra protocol, and Mullvad VPN, which has no IKEv2 option.
Speaking of proprietary protocols:
- NordVPN rolls out NordLynx, a proprietary twist on WireGuard that boosts privacy without sacrificing speed. It also offers NordWhisper, a protocol built to bypass restrictive networks.
- ExpressVPN offers Lightway—one of the fastest protocols available, according to Tom’s Guide.
Meanwhile, VyprVPN relies on Chameleon, Windscribe has WStunnel, and Norton VPN showcases Mimic, all of which obfuscate your VPN traffic to make it look like ordinary HTTPS data.
Cryptography
Cryptography is one of those VPN security features you shouldn’t overlook. It turns your data into code that only you (or someone with the right key) can unlock. Here are its main components minus encryption, which I’ve already covered earlier:
- Key exchange: Allows your device and VPN server to agree on a private key to avoid man-in-the-middle attacks. DH (Diffie-Hellman) creates a shared secret without sending it over the network, while RSA (Rivest-Shamir-Adleman) uses a public–private key pair.
- Message authentication: It uses techniques like HMAC with SHA to check every packet, ensuring that the data leaving your device arrives intact at its destination—and that no one alters it along the way.
- Forward secrecy (perfect forward secrecy/FS): Creates temporary private keys between user devices and VPN servers to ensure that even if someone cracks your encryption key in the future, they still can’t access your past sessions.
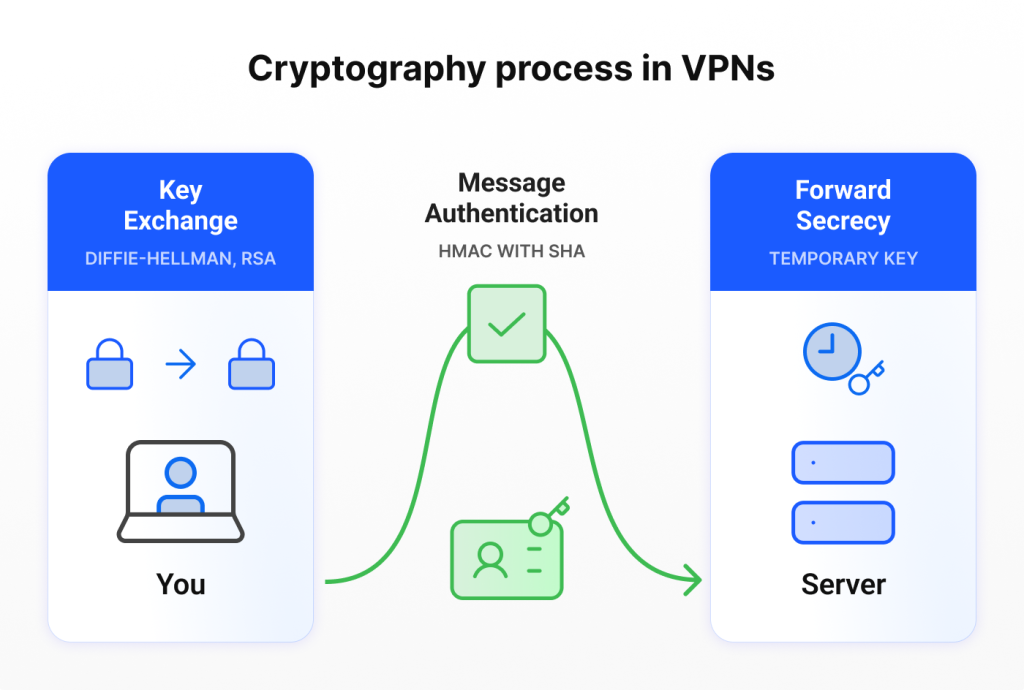
Proton VPN, NordVPN, ExpressVPN, Mullvad, and Windscribe offer Fort Knox-level protection, locking down your data with the latest security standards. PIA, CyberGhost, TunnelBear, VyprVPN, Surfshark, and Hotspot Shield provide reliable security that’s more than enough for typical everyday use. Then there’s Norton VPN, which doesn’t clearly disclose its cryptography features—raising concerns for users who value transparency.
Kill switch
Most VPN providers build their services for stability—but that doesn’t always last A VPN tunnel can drop for a number of reasons, like erratic Wi-Fi, switching networks, server overload, firewall interference—you name it. And when the connection drops, the curtain falls—and anyone watching (at the very least, your ISP and the website admin) can see exactly what you’re doing. Solution? A kill switch.
Technically, it often involves firewall rules or network scripts that detect when your secure tunnel goes down and then immediately block any outbound traffic until the VPN reconnects. In simple words, it automatically disconnects you from the internet if the VPN connection drops, ensuring your data stays yours.
So if your goal is to stay safe, choosing a VPN with a kill switch will get you closer to it. Luckily, almost all the services on our list have this feature in their arsenal.
Note: Even though some VPNs claim to have a kill switch, it’s worth testing it on all platforms you plan to use before going premium, as it may not be supported on certain platforms and protocols—or may even fail to work altogether.
DNS leak protection
Even when your browsing session is encrypted, your most trusted companion—your laptop or a phone—can unwittingly stab you in the back. The thing is that each time you enter a URL or click a link, your device sends a request to a DNS server, basically asking, “What’s the IP address for this website?” Ideally, when connected to a VPN, all these requests should go through the encrypted tunnel to dedicated VPN DNS servers. However, if a DNS leak occurs, your ISP gets a front-row view of the domains you visit.
DNS leak protection makes sure your website lookups stay securely within the encrypted tunnel. If you’re craving details, the VPN client either overrides your operating system’s resolver settings or runs a local DNS proxy on the virtual interface, forcing all DNS queries—whether UDP or TCP—to travel through the tunnel instead of your ISP. It can also disable IPv6 DNS or send those requests through the same secure channel, plugging any potential leak.
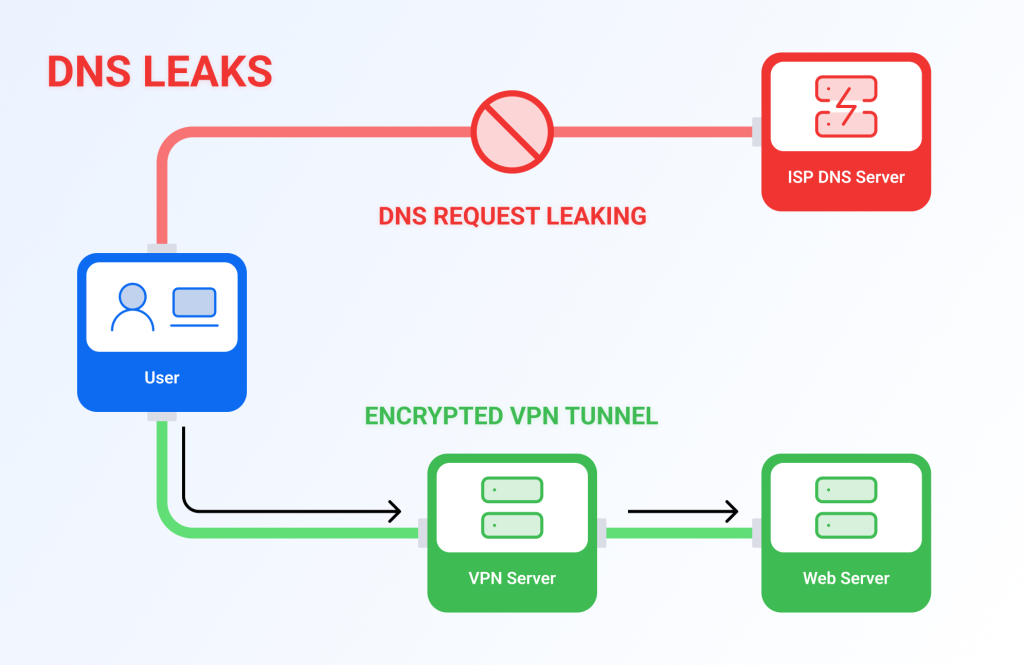
It is one of the few features that every service in our lineup offers, so you can surf the net knowing that your search queries aren’t accidentally broadcasting your interests to the world.
Split tunneling
Split tunneling in VPNs allows you to choose which apps will use your VPN connection and which will connect to the internet directly. It is helpful in cases where you want to bypass restrictions in one application and use your local region or IP address in other environments.
Multi-hop connection (double VPN)
Multi-hop, or double VPN, routes traffic through two or more servers to make it harder to trace your connection on the receiving end but often at the cost of slower speeds. Among the reviewed providers, only Proton VPN, NordVPN, Surfshark, PIA, Windscribe, and Mullvad offer this feature.
Obfuscation
Some actors, like governments, workplaces, and streaming services, don’t take too kindly to VPN users, using their entire arsenal to recognize and restrict VPN traffic. And the primary weapon they use for it is deep packet inspection (DPI), which analyzes the metadata and packet patterns—such as characteristic handshake signals and encryption signatures—to identify data that resembles known VPN protocols. In fact, DPI is so smart that it may spot these unique “fingerprints” even when your data is encrypted.
That’s where obfuscation comes in—it masks or tweaks these packets and metadata, innocently pretending to be regular internet traffic when passing through DPI and firewall checks, which is particularly helpful in regions with strict internet censorship.
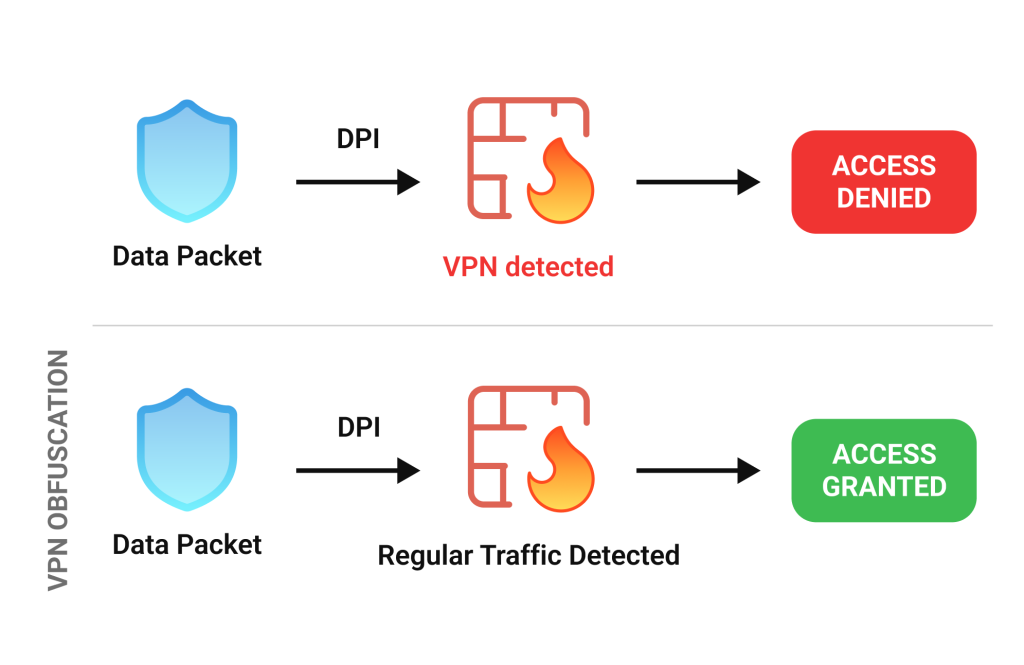
Almost all of the VPNs on our list support this feature, mostly via the Stealth or proprietary protocols. However, PIA offers obfuscation only via proxy, meaning it might not be as reliable as fully integrated solutions, and CyberGhost skips the feature altogether. And although the lack of obfuscation doesn’t always break the deal, users in countries that regularly block VPNs should avoid looking like one.
RAM-only servers
RAM-only servers operate without hard drives and store data only in volatile memory, which automatically erases everything during a reboot. That way, even if someone compromises the server, they won’t find any user data. This is an important point to understand when it comes to VPNs explained through the lens of privacy and security.
Most of the services on our list support this feature—except for Proton VPN, which still uses traditional storage methods deliberately, claiming that “RAM-only VPN servers offer no privacy or security advantages over robust full-disk encryption,” which is a bold statement questioned by users and security experts, since there’s at least one undisputable RAM-only server advantage: if a server is seized, all the data will be erased upon the power-off, leaving no hard evidence you ever used this server, while data stored on an HDD server, though protected, can still be accessed and—which is extremely unlikely but still possible—linked to you.
Price
Finally, there’s the money question. The rule of thumb when we speak about VPNs is “pay up or lose out.” A free VPN may sound appealing, but it always comes at a cost—such as data caps, limited server locations, or fewer available features. And that’s only half the story.
What’s more alarming is that free VPNs may pay the bills by selling—or accidentally exposing—your data. In 2015, Hola VPN infamously sold its free users’ idle bandwidth, enabling a botnet-style attack on 8chan via those shared resources. And in 2023, SuperVPN’s unsecured databases leaked the personal details of over 21 million users—names, email addresses, device IDs, and browsing logs. That’s how badly things can go wrong with “free” VPNs.
And while services like Proton VPN, Windscribe, TunnelBear, and Hotspot Shield generously offer free tiers and all have established, hard-earned reputations that they’re unlikely to risk by selling user data, there’s still a catch. Proton VPN offers a reduced number of server locations and limits a free account to one device only; Hotspot Shield additionally cuts off streaming and gaming support; and Windscribe and TunnelBear both impose data caps on their free plans.
The Verdict: What Is the Best VPN in 2025 for Security?
So, as we’ve explored what encryption and VPN protocols are, how VPNs work in general, and touched on the most important features, what makes a VPN great for security?

To start with, a truly secure VPN should offer strong encryption (AES-256 and ChaCha20 being the best available) and a rich selection of protocols to keep your changing needs covered. It should also ideally include such key VPN security features as a kill switch that automatically cuts off your connection if a VPN tunnel drops and RAM-only servers that ensure that no data gets written to a hard drive.
Note: While other aspects such as jurisdiction, strict no-logs policy, and other features briefly covered in this article matter, we’ll dive deep into privacy in the next article.
But which VPNs from our list check all these boxes?
After digging through all the features, it’s safe to say that NordVPN and ExpressVPN consistently lead the pack with top-tier cryptography, industry-acclaimed proprietary protocols, kill switch feature support, and RAM-only servers. Mullvad, while supporting only OpenVPN and WireGuard protocols, is breathing down their necks with state-of-the-art cryptography.
VyprVPN, with its proprietary Chameleon protocol but a bit less sophisticated encryption, is another strong contender for security.
VPNs like CyberGhost, PIA, and Surfshark are also safe choices, providing dependable, everyday security for most users.
While other VPN providers are also solid in terms of security and can be adopted for everyday tasks like browsing or streaming, they all fall behind in one or more categories. However, among those, Proton VPN deserves an honorable mention. Yes, it lacks RAM-only servers, but it makes up for it with top-tier cryptography, a solid choice of protocols, a reliable kill switch, and a free version with minimal limitations—making it the best free VPN service on our list.
Conclusion
As you may have already noticed, there’s no universal “best” VPN—it all depends on what you need: Are you looking for the fastest or the most private VPN? Or who knows, maybe you run an organization and specifically look for the best VPN for multiple devices? In this article, we’ve only covered one aspect out of many—security—and the right VPN for you will depend on your priorities and how you weigh them.
Up next, we’ll dive into VPN privacy concerns—because while encryption is crucial, true anonymity is a whole different challenge. And meanwhile, if you liked the article, make sure to share it on your socials!